Takecertify shares the latest Cisco CCNP Security 300-206 exam dumps for free exam practice tests and online downloads! “Implementing Cisco Edge Network Security Solutions” 300-206 exam. Ready to pass the 300-206 exam please click https://www.pass4itsure.com/300-206.html (full exam dump)
Cisco 300-206 Exam pdf
[Apr PDF] Free Cisco 300-206 pdf dumps download from Google Drive: https://drive.google.com/open?id=1Flvoq8LGylLRejahm4F5F3vqwCnturmj
[Oct PDF] Free Cisco 300-206 pdf dumps download from Google Drive: https://drive.google.com/open?id=1VC-bIjF8yFyuDvEDbiz0LS0BN4Mn99-M
300-208 SISAS – Cisco: https://www.cisco.com/c/en/us/training-events/training-certifications/exams/current-list/specialist-sisas.html
Cisco 300-206 Online Exam Practice Questions
QUESTION 1
What is the lowest combination of ASA model and license providing 1 Gigabit Ethernet interfaces?
A. ASA 5505 with failover license option
B. ASA 5510 Security+ license option
C. ASA 5520 with any license option
D. ASA 5540 with AnyConnect Essentials License option
Correct Answer: B
QUESTION 2
Which option is a different type of secondary VLAN?
A. Transparent
B. Promiscuous
C. Virtual
D. Community
Correct Answer: D
QUESTION 3
What is the best description of a unified ACL on a Cisco Firewall
A. An Ipv4 ACL with Ipv4 support
B. An ACL the support EtherType in additional Ipv6
C. An ACL with both Ipv4 and Ipv6 functionality
D. An Ipv6 ACL with Ipv4 backward compatitiblity
Correct Answer: C
http://www.cisco.com/c/en/us/td/docs/security/asa/asa90/configuration/guide/asa_90_cli_config/intro_intro.html
QUESTION 4
Choose two correct statements about private-vlan.
A. Interface that is assigned to primary-vlan ID (access mode) can communicate with interface with secondary vlan ID
that belongs to same primary-vlan (same switch)
B. Interface that is assigned to community vlan can communicate with interface in the same secondary vlan but it is also
configured as protected (same switch)
C. You have to configure dhcp snooping for both primary and secondary VLANs
D. You have to configure DAI only for primary vlan
E. You cannot combine private-vlan feature with protected ports ?
Correct Answer: DE
You can enable DHCP snooping on private VLANs. When you enable DHCP snooping on the primary VLAN, it is
propagated to the secondary VLANs. If you configure DHCP snooping on a secondary VLAN, the configuration does not
take
effect if the primary VLAN is already configured. The same statement is true about DAI.
A private-VLAN port cannot be a secure port and should not be configured as a protected port.
QUESTION 5
What are Options of capture command
A. host
B. real-time
C. type
Correct Answer: BC
real-time, type, interface,buffer, match, packet-lenght,trace,circular-buffer, ethernet-type,acces-list, headers-only
QUESTION 6
Which command is the first that you enter to check whether or not ASDM is installed on the ASA?
A. Show ip
B. Show running-config asdm
C. Show running-config boot
D. Show version
E. Show route
Correct Answer: D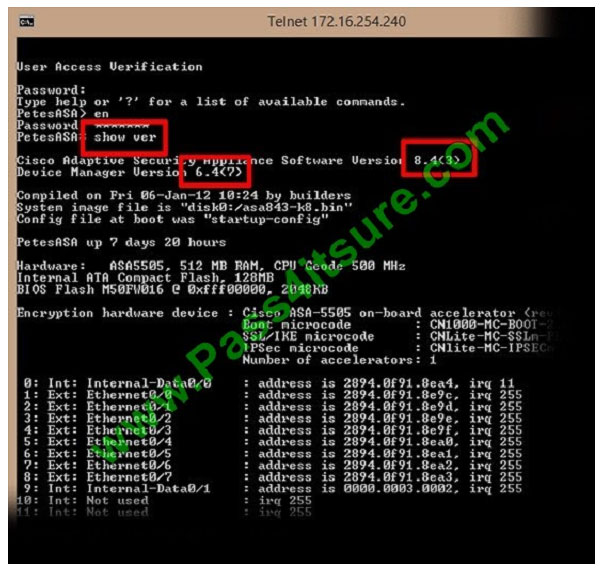
QUESTION 7
Which two option are protocol and tools are used by management plane when using cisco ASA general management
plane hardening ?
A. Unicast Reverse Path Forwarding
B. NetFlow
C. Routing Protocol Authentication
D. Threat detection
E. Syslog
F. ICMP unreachables
G. Cisco URL Filtering
Correct Answer: BE
http://www.cisco.com/web/about/security/intelligence/firewall-best-practices.html

QUESTION 8
CSM (or Prime Infra) Dashboards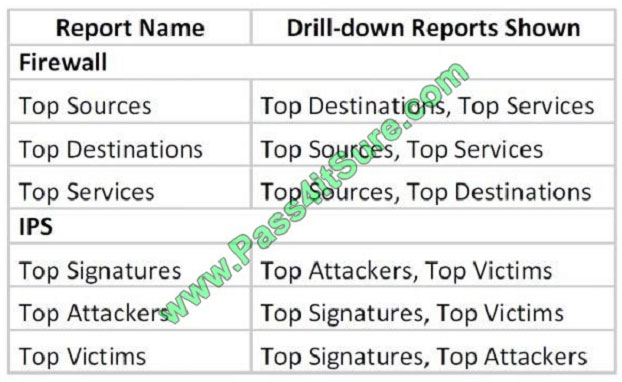
Correct Answer:
Top Destinations –This report ranks the session destinations of all built/deny firewall events received by Security
Manager. The report shows the destination IP address, the count of the number of events for each address, and the
percentage
of the count compared to the sum of all counts in the report. You can click on a data point in the Pie, XY, or Bar graph
that represents a specific destination to see report information about the top sources and top services associated with
that
destination (see Drilling Down into Report Data).
Top Sources –This report ranks the session sources of all built/deny firewall events received by Security Manager. The
report shows the source IP address, the count of the number of events for each address, and the percentage of the
count
compared to the sum of all counts in the report. You can click on a data point in the Pie, XY, or Bar graph that
represents a specific source to see report information about the top destinations and top services associated with that
source (see
Drilling Down into Report Data).
Top Services –This report ranks the destination services of all built/deny firewall events received by Security Manager.
TCP and UDP services include the port number. The report shows the service, the count of the number of events for
each
service, and the percentage of the count compared to the sum of all counts in the report. You can click on a data point in
the Pie, XY, or Bar graph that represents a specific service to see report information about the top destinations and top
sources associated with that service (see Drilling Down into Report Data).
Top Infected Hosts –This report ranks the top infected hosts for traffic originating from infected hosts to black- or gray-
listed sites based on all botnet events received by Security Manager. The report shows the IP address of the infected
host
with the firewall interface name on which the event was detected in parentheses, the count of the number of
connections logged to blacklisted or gray-listed sites for each address, the count of the number of connections that were
blocked
(dropped) by botnet traffic filtering, and the percentage of the count compared to the sum of all counts in the report.
Top Malware Ports –This report ranks the top destination ports for traffic originating from infected hosts to black or gray-
listed sites based on all botnet events received by Security Manager. The report shows the destination malware port,
the
count of the number of connections logged to blacklisted or gray-listed sites for each port, the count of the number of
connections that were blocked (dropped) by botnet traffic filtering, and the percentage of the count compared to the sum
of
all counts in the report.
Top Malware Sites –This report ranks the top botnet sites (black or gray-listed sites) for all inbound and outbound
sessions based on all botnet events received by Security Manager. The report shows the following information:
IP Address–The IP address that is indicated as the malicious host in botnet events, either on the black list or the grey
list.
Malware Site–The domain name or IP address in the dynamic filter database to which the traffic was initiated.
List Type–Whether the site is on the black list or the grey list. Connections Logged–The count of the number of
connections logged or monitored for each site. Connections Blocked–The count of the number of connections that were
blocked
(dropped) by botnet traffic filtering for each site. Threat Level–The botnet threat level for the site, from very low to very
high, or none. Category–The category of threat the site poses as defined in the botnet database, such as botnet,
Trojan,
spyware, and so on.
VPN dashboards
Top Bandwidth Users –This report ranks the VPN users who consumed the most bandwidth. The report shows the
usernames, the bandwidth in total number of bytes sent and received, and the percentage of reported bandwidth used
by
each user.
Top Duration Users –This report ranks the VPN users who remained connected to the network for the longest time. The
report shows the usernames, the connection duration time in days hours:minutes:seconds format, and the percentage
of
the reported duration by each user.
The chart shows duration in seconds.
Top Throughput Users –This report ranks the VPN users who sent and received data at the highest throughput rate.
The report shows the usernames, the throughput for each user in kbps, and the percentage of reported throughput by
each
user. The throughput is calculated as 8.0 *(bandwidth of the user in bytes)/(duration for which the user is connected in
seconds*1000.0).
Connection Profile Report –This report provides a count of user, session, and summary of the bandwidth utilization and
throughput usage for each remote access connection profile. The default report contains this information for all devices
for the previous hour. You can customize the report in several different ways.
User Report –This report provides a summary of the bandwidth utilization, connection duration and throughput usage
for each remote access VPN user. The report shows the usernames, the bandwidth in total number of bytes sent and
received, the connection duration time in days hours:minutes:seconds format, and the throughput for each user in kbps.
The throughput is throughput is calculated as 8.0*(bandwidth of the user in bytes)/(duration for which the user is
connected in seconds*1000.0). Beginning with Security Manager 4.7, the User Report provides both user-level details
and session-level details:
User-Level Details –For a particular user, the user-level details represent the combined value of all that user\\’s
sessions: Username, Total no. of Sessions, Bandwidth, Duration, and Throughput. Session-Level Details –Expanding
the tree
displays the session-level details for each session that a particular user has a VPN connection with; the session-level
details encompass the Session ID, Login Time, Logout Time, Bandwidth, Throughput, and Duration of the Session.
(Here
the logout time is calculated by using the formula Logout Time = Login Time + Duration.)
QUESTION 9
What are two reasons to implement Cisco IOS MPLS Bandwidth-Assured Layer 2 Services? (Choose two.)
A. guaranteed bandwidth and peak rates as well as low cycle periods, regardless of which systems access the device
B. increased resiliency through MPLS FRR for AToM circuits and better bandwidth utilization through MPLS TE
C. enabled services over an IP/MPLS infrastructure, for enhanced MPLS Layer 2 functionality
D. provided complete proactive protection against frame and device spoofing
Correct Answer: BC
QUESTION 10
Which three options are hardening techniques for Cisco IOS routers? (Choose three.)
A. limiting access to infrastructure with access control lists
B. enabling service password recovery
C. using SSH whenever possible
D. encrypting the service password
E. using Telnet whenever possible
F. enabling DHCP snooping
Correct Answer: ACD
QUESTION 11
What is the default behavior of NAT control on Cisco ASA Software Version 8.3?
A. NAT control has been deprecated on Cisco ASA Software Version 8.3.
B. It will prevent traffic from traversing from one enclave to the next without proper access configuration.
C. It will allow traffic to traverse from one enclave to the next without proper access configuration.
D. It will deny all traffic.
Correct Answer: A
QUESTION 12
Which URL matches the regex statement “http”*/”www.cisco.com/”*[^E]”xe”?
A. https://www.cisco.com/ftp/ios/tftpserver.exe
B. https://cisco.com/ftp/ios/tftpserver.exe
C. http:/www.cisco.com/ftp/ios/tftpserver.Exe
D. https:/www.cisco.com/ftp/ios/tftpserver.EXE
Correct Answer: A
QUESTION 13
Which three configurations tasks do you perform to allow Not Flow on a Cisco ASA G500 Series firewall? (Choose
three)
A. Apply the newly created class map to the global policy.
B. Enable NetFlow Version 9.
C. Create a class map match interesting traffic.
D. Create an ACL to allow UDP traffic on port 9996.
E. Define a NetFlow collector by using the flow-export command.
F. Apply NetFlow Exporter to the outside interface in the inbound direction
Correct Answer: ACE
Share Pass4itsure discount codes for free
About Pass4itsure!
Pass4itsure offers the latest exam practice questions and answers free of charge! Update all exam questions throughout the year,
with a number of professional exam experts! To make sure it works! Maximum pass rate, best value for money! Helps you pass the exam easily on your first attempt.
Summarize:
How do I pass the Cisco 300-206 exam? You need to be prepared for it!
You need the latest and most effective learning materials and proper practices to pass the 300-206 exam. “This exam tests whether a network security engineer knows the components and architecture of secure access, by utilizing 802.1X and Cisco TrustSec. This exam assesses knowledge of Cisco Identity Services Engine (ISE) architecture, solution, and components as an overall network threat mitigation and endpoint control solution. It also includes the fundamental concepts of bringing your own device (BYOD) using posture and profiling services of ISE”. Pass4itsure offers you the latest exam materials! You can use the materials to prepare to help you achieve excellent results!