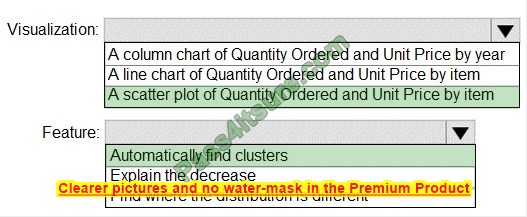
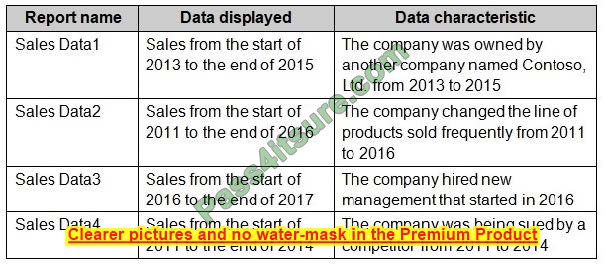
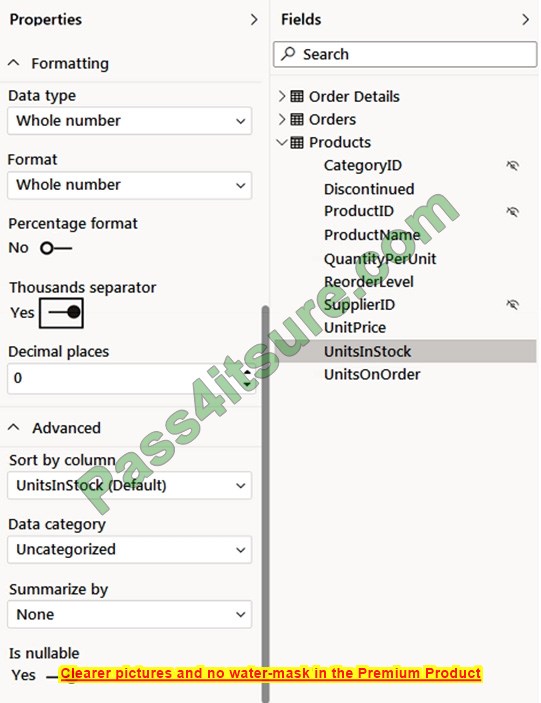
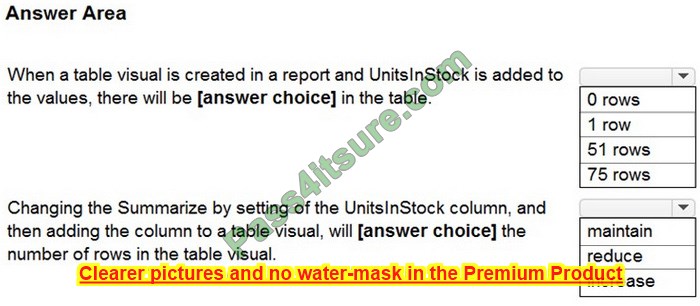
What is the method of the AZ-800 exam, how you prepare strongly determines how quickly you succeed in the Microsoft AZ-800 exam. It is recommended that you use here new AZ-800 dumps practice questions.
Download new AZ-800 dumps practice questions 153+ https://www.pass4itsure.com/az-800.html (pdf+vce) to get you quickly past the Administering Windows Server Hybrid Core Infrastructure exam.
Other ways to prepare: AZ-800 exam
Of course, it’s not to say that other ways to prepare for the exam AZ-800 are wrong, you’d better combine other ways with dumps to prepare.
Try these ways:
- Take advantage of the official exam guide
- Make a study plan
- Take the AZ-800 practice test
- Participate in a training program
- Join a discussion group
…
There are many more, and I have only listed the most common ones.
The AZ-800 exam has been updated on April 25, 2024
This message all the more means that you need new AZ-800 dumps practice questions to prepare for the exam, remember, it must be new, outdated AZ-800 exam questions are useless.
Back to the topic, here is the focus on the new changes in the exam:
You can check the official information here.
New AZ-800 exam new materials to share:
It is divided into document mode
- Study guide for Exam AZ-801: Configuring Windows Server Hybrid Advanced Services
- Exam AZ-800: Administering Windows Server Hybrid Core Infrastructure – Certifications
- Exam AZ-801: Configuring Windows Server Hybrid Advanced Services – Certifications
- Microsoft Certified: Windows Server Hybrid Administrator Associate – Certifications
It is divided into video modes
- https://learn.microsoft.com/en-us/shows/exam-readiness-zone/preparing-for-az-800-deploy-and-manage-active-directory-domain-services-as-ds-in-on-premises-and-cloud-environments-segment-1-of-5
- https://learn.microsoft.com/en-us/shows/exam-readiness-zone/preparing-for-az-800-manage-windows-servers-and-workloads-in-a-hybrid-environment-segment-2-of-5
- https://learn.microsoft.com/en-us/shows/exam-readiness-zone/preparing-for-az-800-manage-virtual-machines-and-containers-segment-3-of-5
- https://learn.microsoft.com/en-us/shows/exam-readiness-zone/preparing-for-az-800-implement-and-manage-an-on-premises-and-hybrid-networking-infrastructure-segment-4-of-5
- https://learn.microsoft.com/en-us/shows/exam-readiness-zone/preparing-for-az-800-manage-storage-and-file-services-segment-5-of-5
It is divided into book mode
- Exam Ref AZ-800 Administering Windows Server Hybrid Core Infrastructure
- Administering Windows Server Hybrid Core Infrastructure AZ-800 Exam Guide: Design, implement, and manage Windows Server core infrastructure on …
All three are common modes and you can choose your preferred one to take the AZ-800 exam.
Share new AZ-800 dumps some free AZ-800 practice questions
Come from: Pass4itSure
Number of Questions: 15/215
Relevant certification: Microsoft
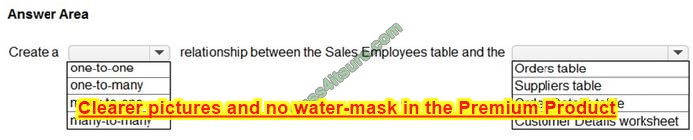
Question 1:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
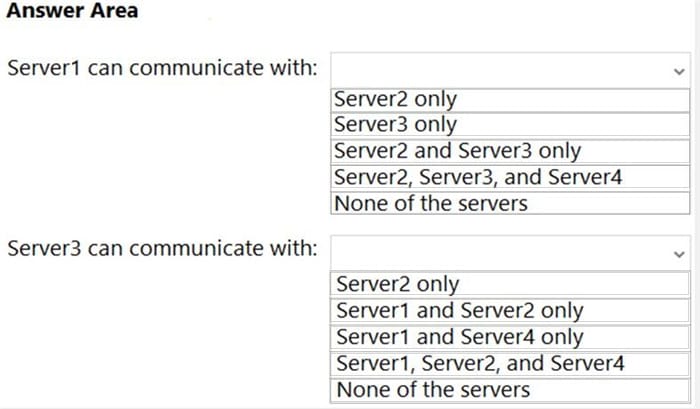
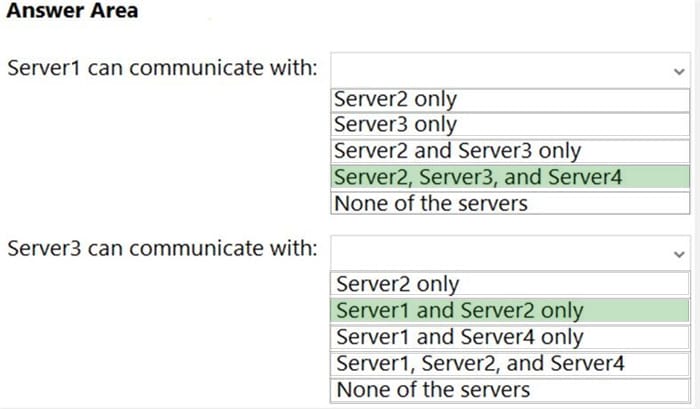
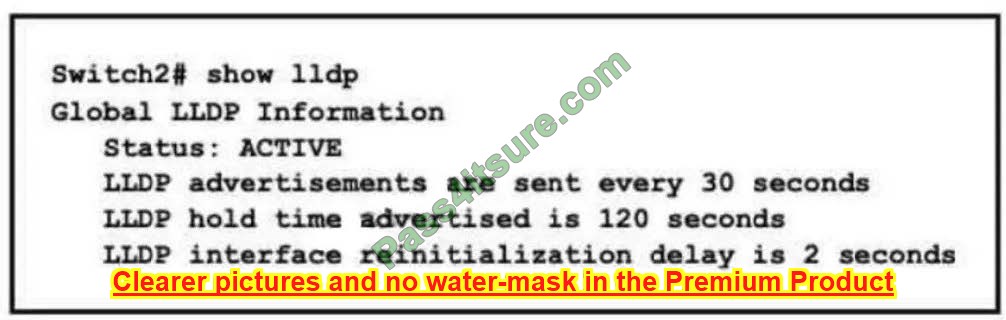
Your network contains an Active Directory Domain Services (AD DS) forest. The forest contains three Active Directory sites named Site1, Site2, and Site3. Each site contains two domain controllers. The sites are connected by using
DEFAULTIPSITELINK.
You open a new branch office that contains only client computers.
You need to ensure that the client computers in the new office are primarily authenticated by the domain controllers in Site1.
Solution: You create a new site named Site4 and associate Site4 to DEFAULTSITELINK.
Does this meet the goal?
A. Yes
B. No
Correct Answer: B
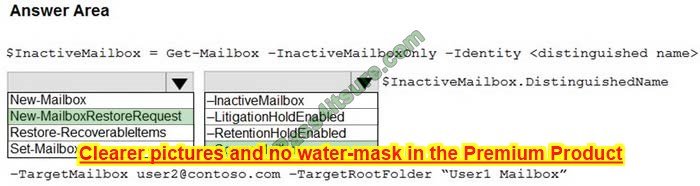
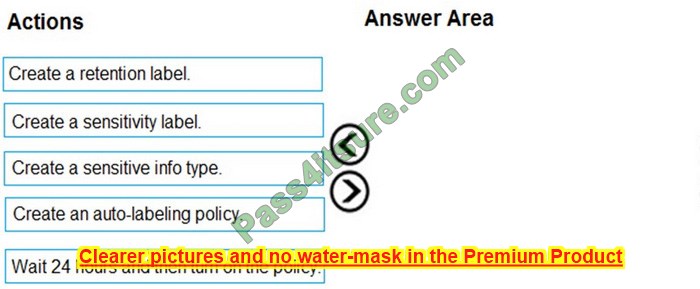
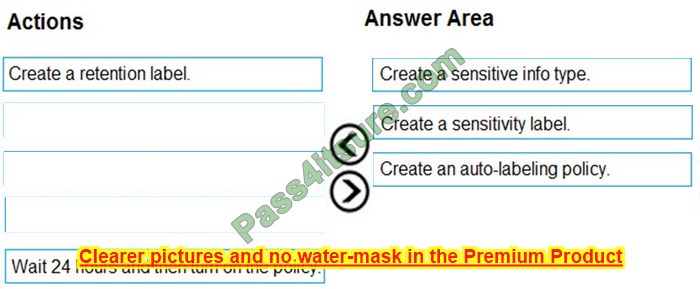
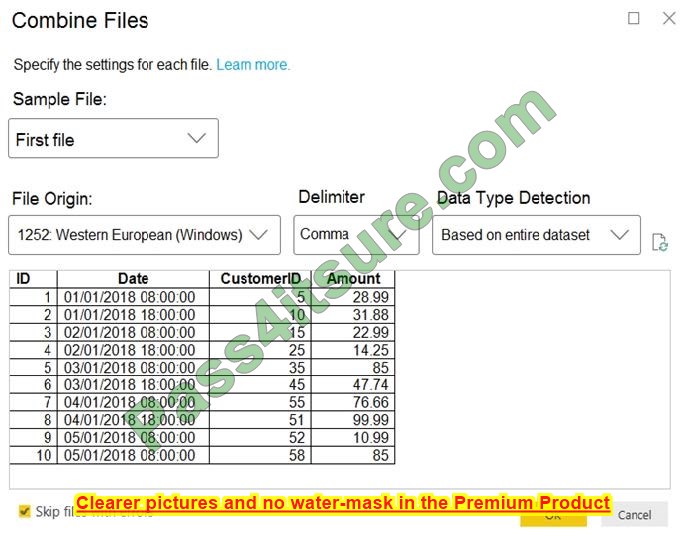
Question 2:
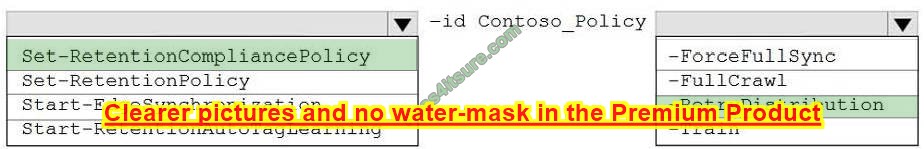
DRAG DROP
You deploy a single-domain Active Directory Domain Services (AD DS) forest named contoso.com.
You deploy a server to the domain and configure the server to run a service.
You need to ensure that the service can use a group-managed service account (gMSA) to authenticate.
Which three PowerShell cmdlets should you run in sequence? To answer, move the appropriate cmdlets from the list of cmdlets to the answer area and arrange them in the correct order.
Select and Place:
Correct Answer:
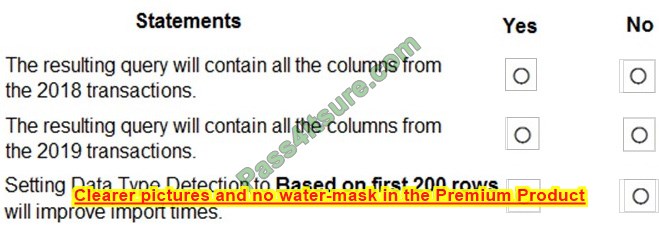
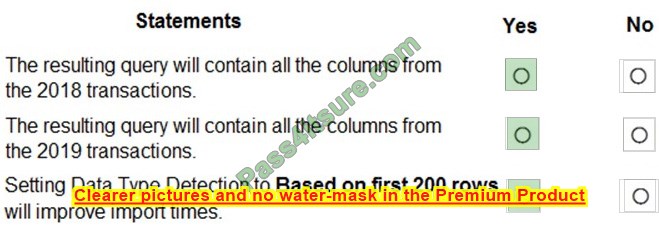
Question 3:
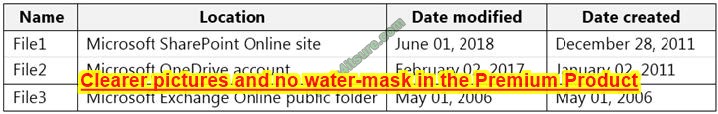
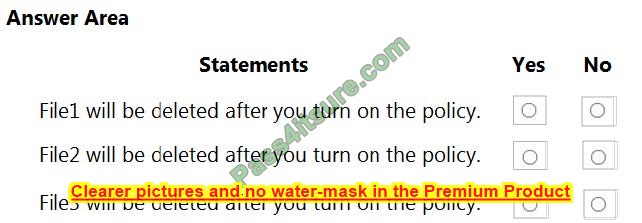
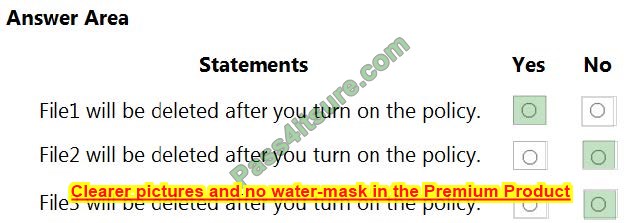
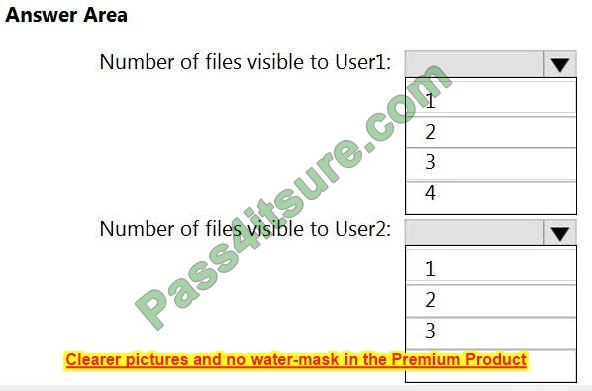
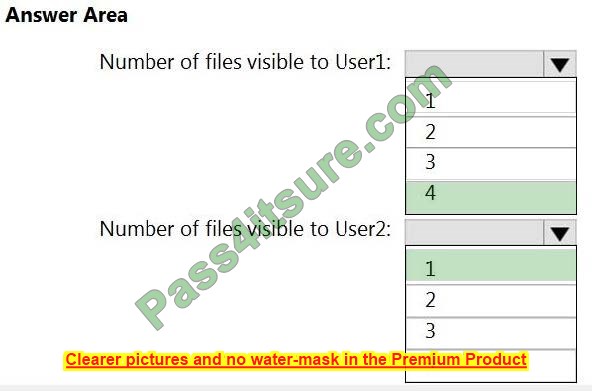
You need to meet the technical requirements for Server1. Which users can currently perform the required tasks?
A. Admin1 only.
B. Admin3 only.
C. Admin1 and Admin3 only.
D. Admin1, Admin2 and Admin3.
Correct Answer: C
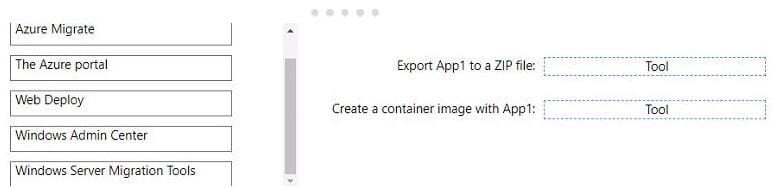
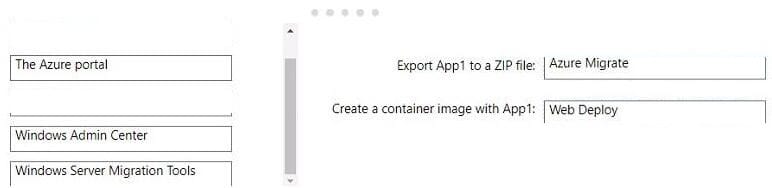
Question 4:
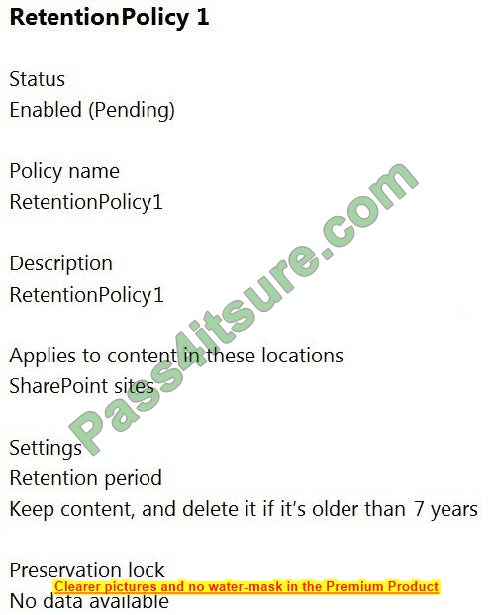
You need to use the principle of least privilege.
Choose a solution to meet the technical requirements of User1.
A. Create a delegation on contoso.com.
B. Create a delegation on OU3.
C. Add Users1 to the Server Operators group in contoso.com.
D. Add Users1 to the Account Operators group on contoso.com.
Correct Answer: B
Question 5:
You need to meet the technical requirements for User1. The solution must use the principle of least privilege. What should you do?
A. Add Users1 to the Server Operators group in contoso.com.
B. Create a delegation on contoso.com.
C. Add Users1 to the Account Operators group on contoso.com.
D. Create a delegation on OU3.
Correct Answer: D
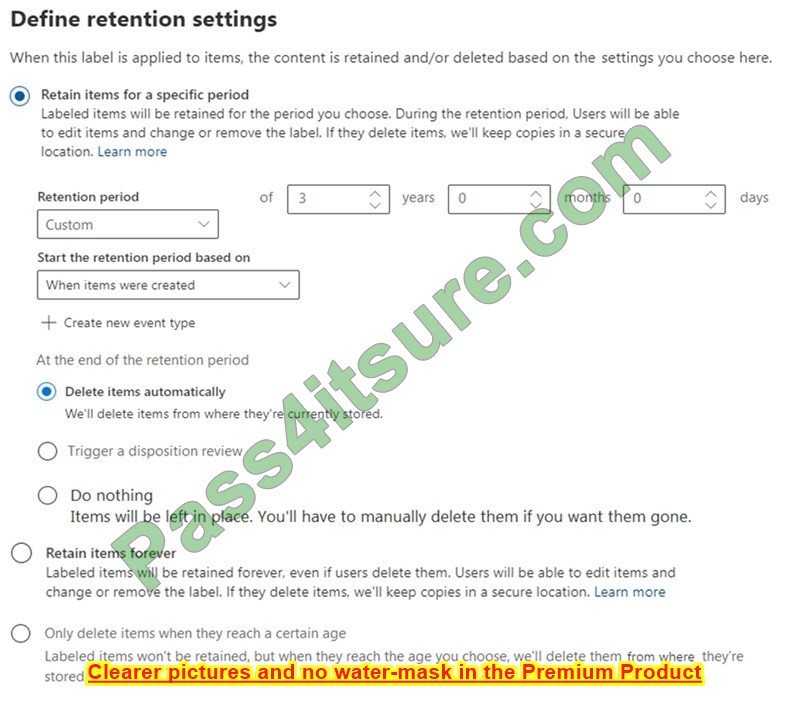
Question 6:
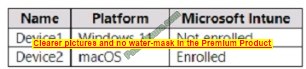
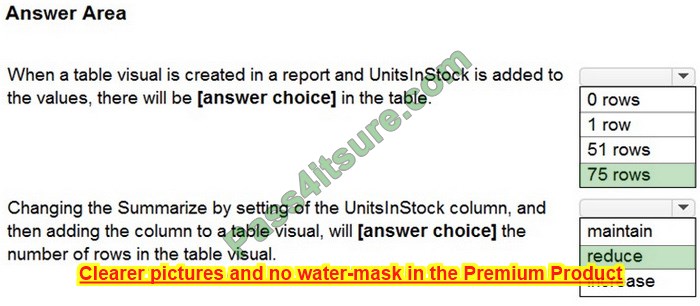
HOTSPOT
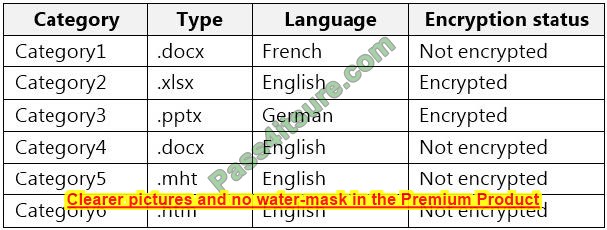
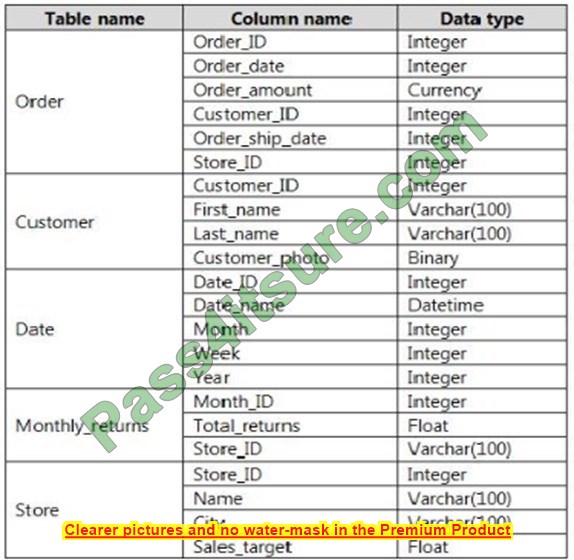
You have a file server named Server1 that runs Windows Server and contains the volumes shown in the following table.
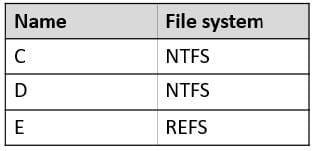
On which volumes can you use BitLocker Drive Encryption (BitLocker) and disk quotas? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
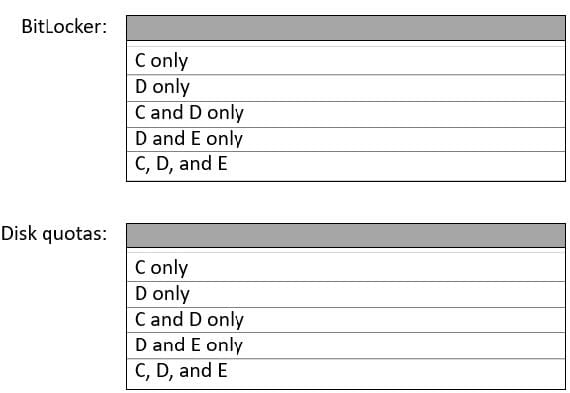
Correct Answer:

Reference: https://docs.microsoft.com/en-us/windows-server/storage/refs/refs-overview
Question 7:
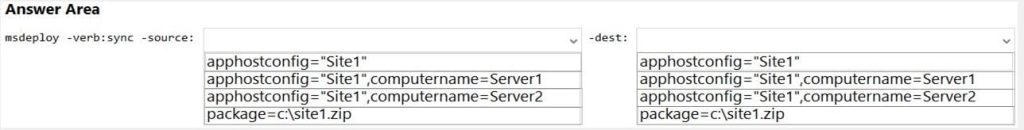
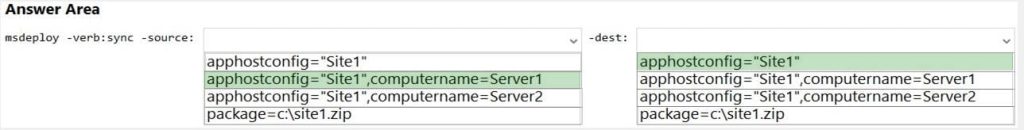
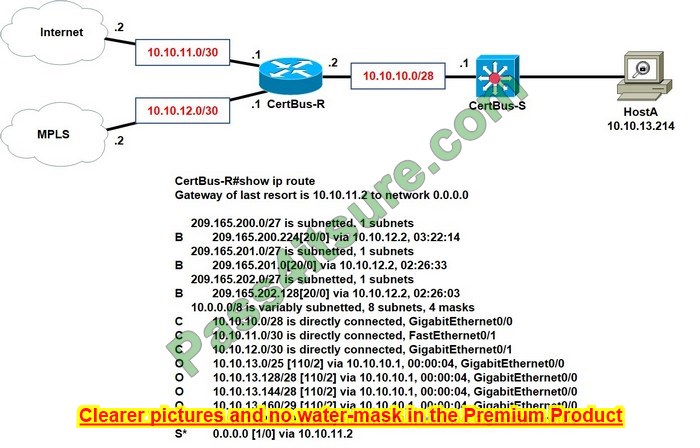
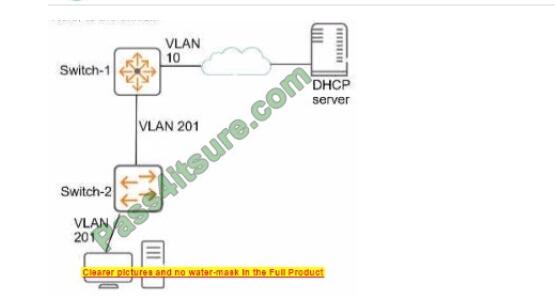
You have servers that have the DNS Server role installed. The servers are configured as shown in the following table.
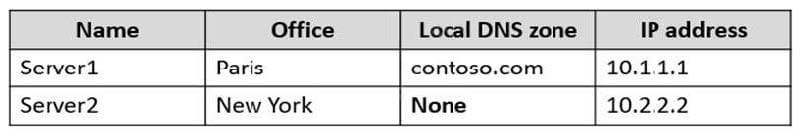
All the client computers in the New York office use Server2 as the DNS server.
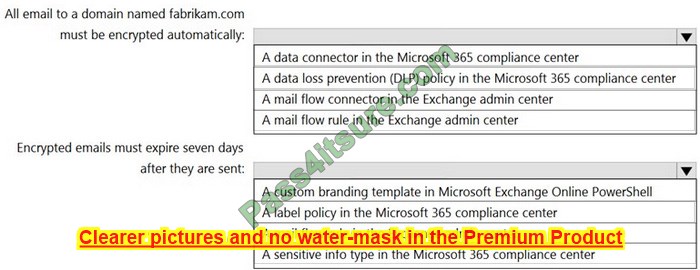
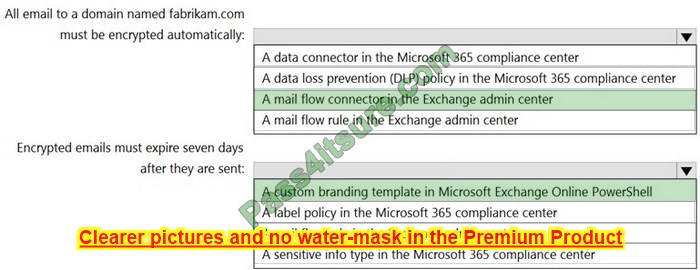
You need to configure name resolution in the New York office to meet the following requirements:
1. Ensure that the client computers in New York can resolve names from contoso.com.
2. Ensure that Server2 forwards all DNS queries for internet hosts to 131. 107.100.200.
The solution must NOT require modifications to Server1.
Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. a forwarder
B. a conditional forwarder
C. a delegation
D. a secondary zone
E. a reverse lookup zone
Correct Answer: AB
A conditional forwarder is required for contoso.com.
A forwarder is required for all other domains.
When you have a conditional forwarder and a forwarder configured, the conditional forwarder will be used for the specified domain.
You could use a secondary zone for contoso.com but that would require a configuration change on Server1.
Question 8:
HOTSPOT
You have an Azure subscription named sub1 and 500 on-premises virtual machines that run Windows Server.
You plan to onboard the on-premises virtual machines to Azure Arc by running the Azure Arc deployment script.
You need to create an identity that will be used by the script to authenticate access to sub1. The solution must use the principle of least privilege.
How should you complete the command? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer:

Reference: https://docs.microsoft.com/en-us/azure/azure-arc/servers/onboard-service-principal
Question 9:
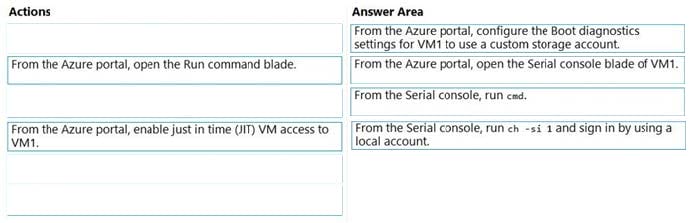
You need to configure remote administration to meet the security requirements. What should you use?
A. an Azure Bastion host
B. Azure AD Privileged Identity Management (PIM)
C. the Remote Desktop extension for Azure Cloud Services
D. just in time (JIT) VM Access
Correct Answer: D
Question 10:
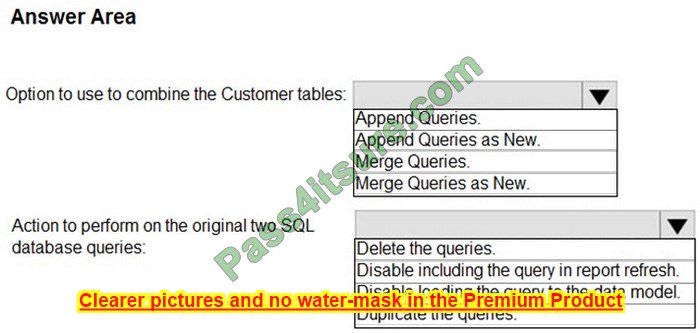
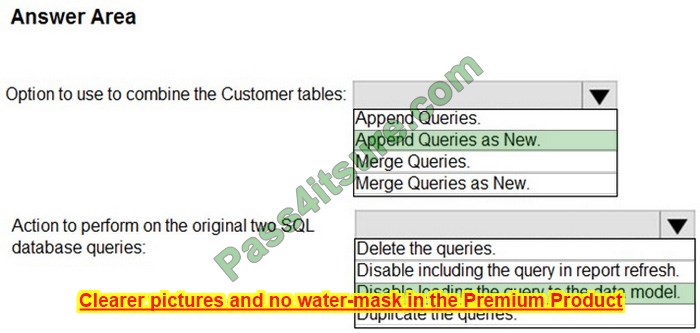
DRAG DROP
You have a server named Server1 that has Windows Admin Center installed. The certificate used by Windows Admin Center was obtained from a certification authority (CA).
The certificate expires.
You need to replace the certificate.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:
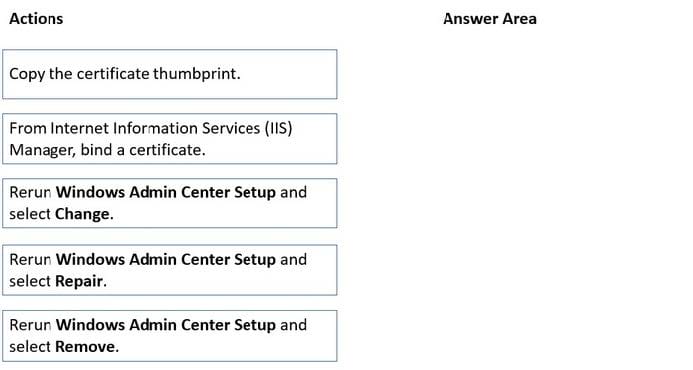
Correct Answer:
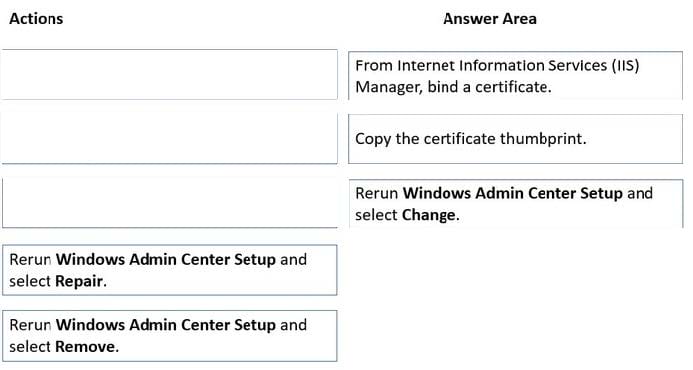
Reference: https://www.starwindsoftware.com/blog/change-the-windows-admin-center-certificate
Question 11:
You are planning the implementation of Azure Arc to support the planned changes.
You need to configure the environment to support configuration management policies.
What should you do?
A. Hybrid Azure AD joins all the servers.
B. Create a hybrid runbook worker for Azure Automation.
C. Deploy the Azure Connected Machine agent to all the servers.
D. Deploy the Azure Monitor agent to all the servers.
Correct Answer: C
Reference: https://docs.microsoft.com/en-us/azure/azure-arc/servers/plan-at-scale-deployment
Question 12:
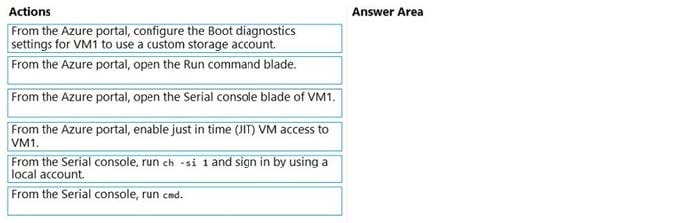
DRAG DROP
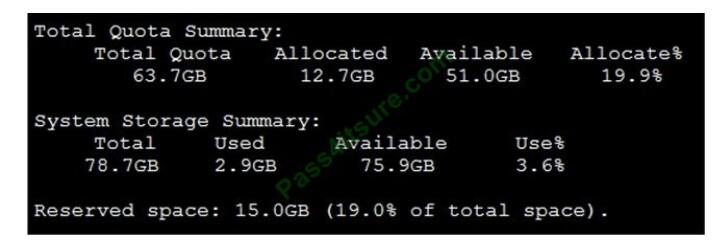
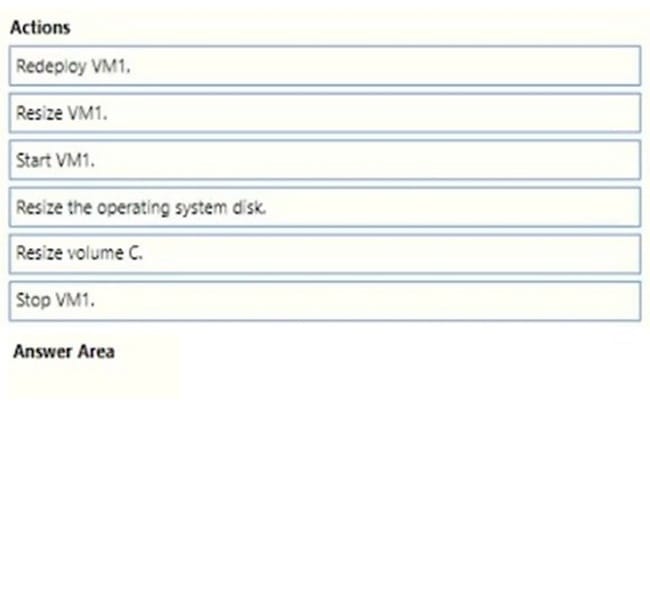
You have an Azure subscription. The subscription contains a virtual machine named VM1 that runs Windows Server. VM1 contains a 128-GB operating system disk.
You need to increase the size of volume C on VM1 to 250 GB.
Which four actions should you perform in sequence?
To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:
Correct Answer:
How to expand virtual hard disks attached to a Windows virtual machine
You may need to expand the OS disk if you\’re supporting a legacy application that installs components on the OS disk or if you\’re migrating a physical PC or VM from on-premises that has a larger OS disk.
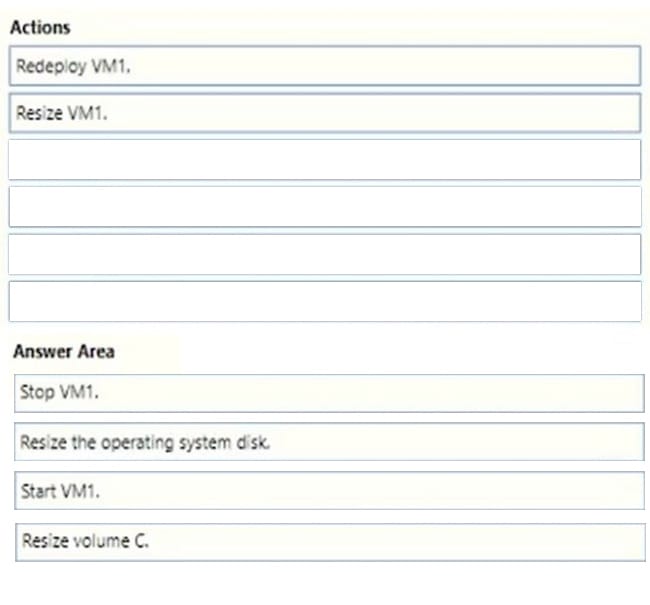
Step 1: Stop VM1.
Resize a managed disk by using PowerShell
1. Stop the VM before resizing the disk:
Stop-AzVM -ResourceGroupName $rgName -Name $vmName
Step 2: Resize the operating system disk.
2. Obtain a reference to the managed OS disk. Set the size of the managed OS disk to the desired value and update the Disk:
$disk= Get-AzDisk -ResourceGroupName $rgName -DiskName $diskName $disk.DiskSizeGB = 1023 Update-AzDisk -ResourceGroupName $rgName -Disk $disk -DiskName $disk.Name
Step 3: Start VM1.
3. Updating the VM might take a few seconds. When the command finishes executing, restart the VM:
Start-AzVM -ResourceGroupName $rgName -Name $vmName
Step 4: Resize Volume C.
Expand the volume in the operating system
When you\’ve expanded the disk for the VM, you need to go into the OS and expand the volume to encompass the new space.
Reference: https://learn.microsoft.com/en-us/azure/virtual-machines/windows/expand-os-disk
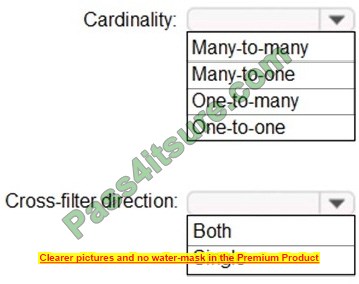
Question 13:
DRAG DROP
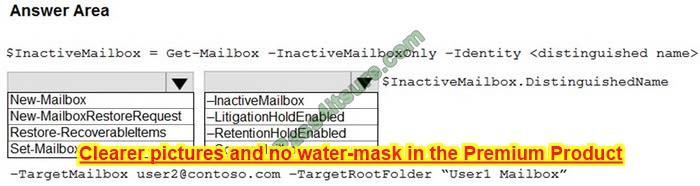
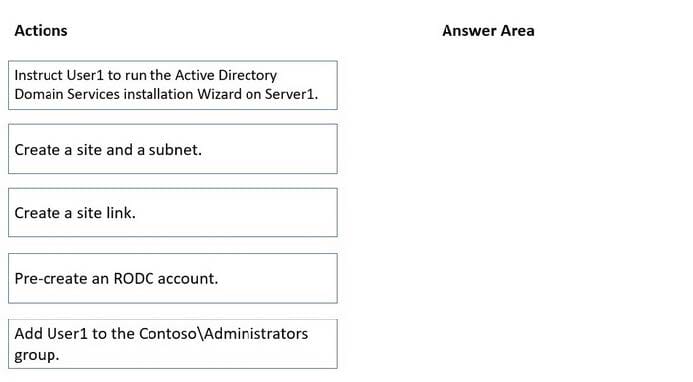
Your network contains a single domain Active Directory Domain Services (AD DS) forest named contoso.com. The forest contains a single Active Directory site.
You plan to deploy a read-only domain controller (RODC) to a new data center on a server named Server1. A user named User1 is a member of the local Administrators group on Server1.
You need to recommend a deployment plan that meets the following requirements:
1. Ensures that a user named User1 can perform the RODC installation on Server1
2. Ensures that Server1 is in a new site named RemoteSite1
3. Uses the principle of least privilege
Which three actions should you recommend performing in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:
Correct Answer:
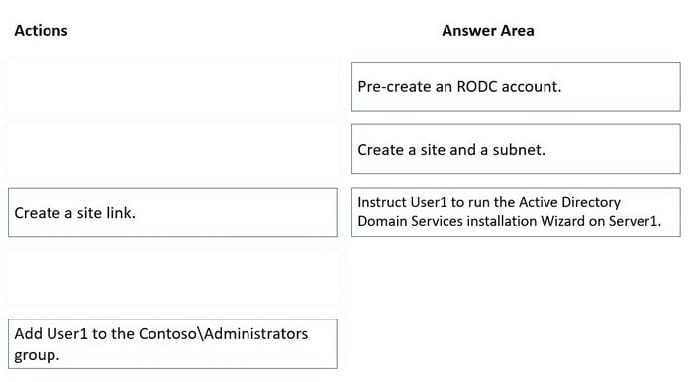
Step 1: Pre-create an RODC account.
You can deploy RODC using the Staged feature. It consists of pre-creating the RODC computer account in the ADUC console and basic setup.
Step 2: Create a site and a subnet
Step 3: Instruct User1 to run the Active Directory Domain Services installation Wizard on Server1.
The Domain Controller Options page also enables you to choose the appropriate Active Directory logical site name from the forest configuration. By default, it selects the site with the most correct subnet. If there is only one site, it selects that site automatically.
Important:
If the server does not belong to an Active Directory subnet and there is more than one Active Directory site, nothing is selected and the Next button is unavailable until you choose a site from the list.
Incorrect:
* Add User1 to the Contoso\Administrators group.
This is against the principle of least privilege.
Reference:
https://woshub.com/deploying-read-domain-controller-windows-server-2016/
Question 14:
You need to configure the Group Policy settings to ensure that the Azure Virtual Desktop session hosts meet the security requirements. What should you configure?
A. loopback processing in GPO4
B. security filtering for the link of GPO1
C. loopback processing in GPO1
D. The enforced property for the link of GPO4
E. the Enforced property for the link of GPO1
F. security filtering for the link of GPO4
Correct Answer: A
Question 15:
SIMULATION You need to collect errors from the System event log of SRV1 to a Log Analytics workspace.
The required source files are located in a folder named \\dc1.contoso.com\install.
To complete this task, sign in the required computer or computers.
A. See the explanation below.
B. PlaceHolder
C. PlaceHolder
D. PlaceHolder
Correct Answer: A
Configure Windows event logs
Configure Windows event logs from the Agents configuration menu for the Log Analytics workspace.
Step 1: Go to the Log Analytics workspaces menu in the Azure portal.
Configure data sources
To configure data sources for Log Analytics agents, go to the Log Analytics workspaces menu in the Azure portal and select a workspace.
Step 2: Select Agents configuration.
Step 3: Select the tab for the data source you want to configure.
In this case the Windows event log of SRV1.
Step 4: Select only the Error option in the System Log row.
Azure Monitor only collects events from Windows event logs that are specified in the settings.
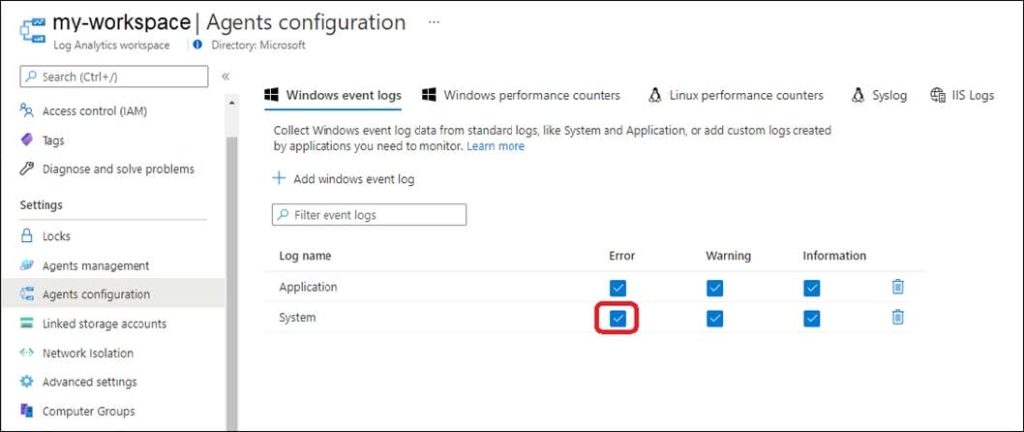
Reference: https://learn.microsoft.com/en-us/azure/azure-monitor/agents/data-sources-windows-events https://learn.microsoft.com/en-us/azure/azure-monitor/agents/agent-data-sources#configure-data-sources
More Microsoft Exam Questions…
Answers to your most important AZ-800 questions
How can I pass the AZ-800 exam quickly?
Advice to follow (two things) 1. Study the official guide 2. New AZ-800 dumps practice test (the most important and mandatory):
I recommend getting it from Pass4itSure. That’s great for this purpose.
What are the best tips, tools, or resources for the AZ-800 exam?
Still is new AZ-800 dumps practice questions.
If you want to get the AZ-800 exam quickly, the new AZ-800 dumps practice questions are essential.
Go to the new AZ-800 dumps (pdf+vce) now https://www.pass4itsure.com/az-800.html get more Microsoft new AZ-800 practice questions to pass the exam easily.