What are the best online resources for the Cisco CCNA Certification 200-301 exam? Today we are proud to introduce Pass4itSure to you, the updated 200-301 dumps 2023, the best online resource for all your needs.
The latest 200-301 dumps https://www.pass4itsure.com/200-301.html will give you the latest exam questions and answers to help you crack the CCNA 200-301 exam.
How do I prepare for Cisco CCNA 200-301 certification?
It’s not challenging and you can crack it, provided that you use the right method.
There are so many ways to learn 200-301.
On the Internet – You can start online. You just put your query and get the best solution.
Video – You can watch the film and learn from it.
Forum: – You should use experts in solutions obtained on the forum website.
Books:- You can purchase books online and start learning.
However, it is recommended that you practice with our Pass4itSure 200-301 dumps to prepare for the exam.
What is the difficulty of the 200-301 exam?
The 200-301 exam is part of the Cisco CCNA certification and covers networking fundamentals, IP protocols, routing, and switching. , the exam is difficult, and it is necessary to fully understand various concepts and techniques and master their application.
To overcome this difficulty, you need the latest 200-301 exam questions, don’t worry, we share them with you (Pass4itSure) provided.
Pass4itsure 2023 Newest Cisco 200-301 CCNA Exam Questions Answers
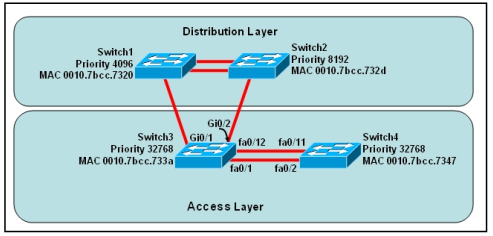
Q1:
Refer to the exhibit.
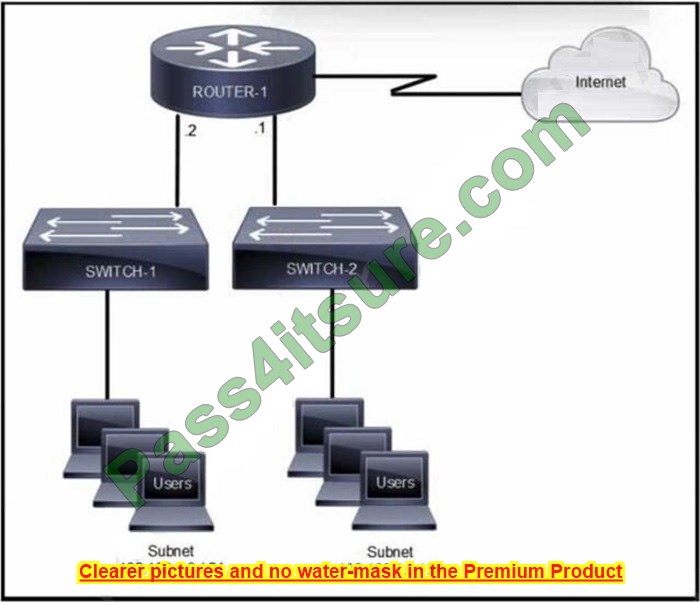
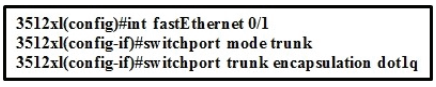
access-list 10 permit 192.168.0.0 0.0.0.255
ip nat inside source list 10 pool CCNA overload
Which command set configures ROUTER-1 to allow Internet access for users on the 192.168.1.0/24 subnet while using 209.165.202.129 for Port Address Translation?
A. ip nat pool CCNA 192.168.0.0 192.168.1.255 netmask 255.255.255.0
B. ip nat pool CCNA 209.165.202.129 209.165.202.129 netmask 255.255.255.255
access-list 10 permit 192.168.1.0 255.255.255.0
ip nat inside source list 10 pool CCNA overload
C. ip nat pool CCNA 192.168.0.0 192.168.1.255 netmask 255.255.255.0
access-list 10 permit 192.168.0.0 255.255.255.0
ip nat inside source list 10 pool CCNA overload
D. ip nat pool CCNA 209.165.202.129 209.165.202.129 netmask 255.255.255.255 access-list 10 permit 192.168.1.0 0.0.0.255 ip nat inside source list 10 pool CCNA overload
Correct Answer: A
Q2:
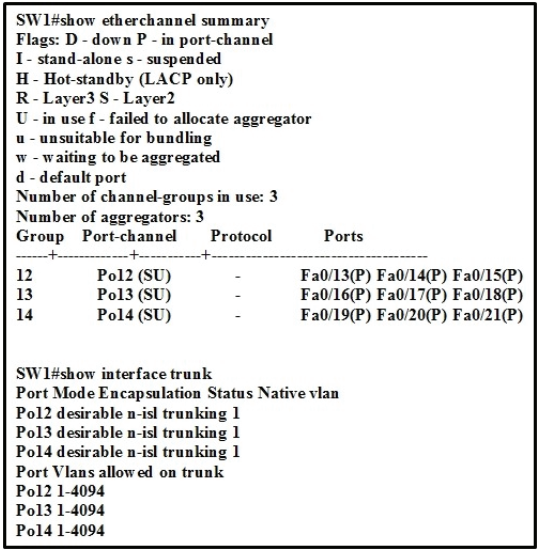
Refer to the exhibit. Site A was recently connected to site B over a new single-mode fiber path. Users at site A report Intermittent connectivity Issues with applications hosted at site B. What is the reason for the problem?

A. Heavy usage is causing high latency.
B. An incorrect type of transceiver has been inserted into a device on the link.
C. physical network errors are being transmitted between the two sites.
D. The wrong cable type was used to make the connection.
Correct Answer: C
Q3:
A multivendor network exists and the company is implementing VoIP over the network for the first time.

A. Option A
B. Option B
C. Option C
D. Option D
Correct Answer: B
Q4:
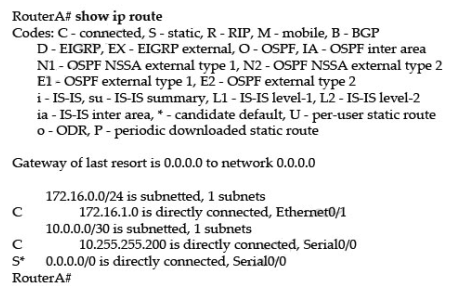
Which two statements are factual about the command ip route 172.16.3.0 255.255.255.0 192.168.2.4? (Choose two.)
A. It establishes a static route to the 172.16.3.0 network.
B. It establishes a static route to the 192.168.2.0 network.
C. It configures the router to send any traffic for an unknown destination to the 172.16.3.0 network.
D. It configures the router to send any traffic for an unknown destination out the interface with the address 192.168.2.4.
E. It uses the default administrative distance.
F. It is a route that would be used last if other ways to the same destination exist.
Correct Answer: AE
Q5:
What is a feature of WPA?
A. 802.1x authentication
B. preshared key
C. TKIP/MIC encryption
D. small Wi-Fi application
Correct Answer: A
Q6:
DRAG DROP
Drag and drop the threat-mitigation techniques from the left onto the types of threat or attack they mitigate on the right.
Select and Place:

Correct Answer:

Double-Tagging attack:
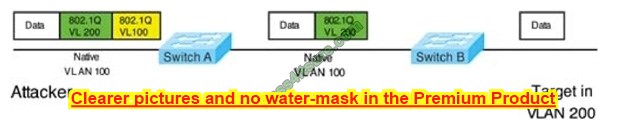
In this attack, the attacking computer generates frames with two 802.1Q tags. The first tag matches the native VLAN of the trunk port (VLAN 10 in this case), and the second matches the VLAN of a host it wants to attack (VLAN 20).
When the packet from the attacker reaches Switch A, Switch A only sees the first VLAN 10 and it matches with its native VLAN 10 so this VLAN tag is removed.
Switch A forwards the frame out of all links with the same native VLAN 10. Switch Receives the frame with a tag of VLAN 20 so it removes this tag and forwards it out to the Victim’s computer.
Note: This attack only works if the trunk (between two switches) has the same native VLAN as the attacker.
To mitigate this type of attack, you can use VLAN access control lists (VACLs, which apply to all traffic within a VLAN. We can use VACL to drop attacker traffic to specific victims/servers) or implement Private VLANs.
ARP attack (like ARP poisoning/spoofing) is a type of attack in which a malicious actor sends falsified ARP messages over a local area network as ARP allows a gratuitous reply from a host even if an ARP request was not received.
This results in linking an attacker\’s MAC address with the IP address of a legitimate computer or server on the network. This is an attack based on ARP which is at Layer 2. Dynamic ARP inspection (DAI) is a security feature that validates ARP packets in a network which can be used to mitigate this type of attack.
Q7:
Which switch concept is used to create separate broadcast domains?
A. STP
B. VTP
C. VLAN
D. CSMA/CD
Correct Answer: C
Q8:
Refer to the exhibit. A network engineer must update the configuration on Switch2 so that it sends LLDP packets every minute and the information sent via LLDP is refreshed every 3 minutes Which configuration must the engineer apply?
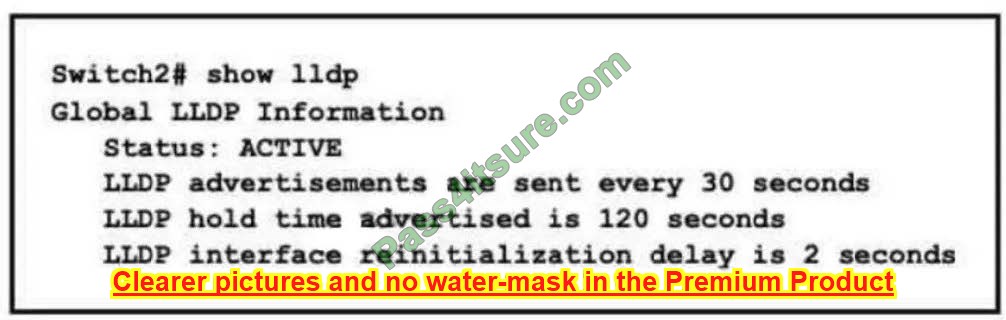
A. Switch2(config)#lldp timer 60 Switch2(config)#lldp holdtime 180
B. Switch2(config)#lldp timer 60 Switch2(config)#lldp tlv-select 180
C. Switch2(config)#lldp timer 1 Switch2(config)#lldp holdtime 3
D. Switch2(config)#lldp timer 1 Switch2(config)#lldp tlv-select 3
Correct Answer: A
Q9:
When using Rapid PVST+, which command guarantees the switch is always the root bridge for VLAN 200?
A. spanning-tree vlan 200 priority 614440
B. spanning-tree vlan 200 priority 38572422
C. spanning-tree vlan 200 priority 0
D. spanning-tree vlan 200 root primary
Correct Answer: C
Q10:
A network engineer implements a new Cisco Firepower device on the network to exploit its intrusion detection functionality. There is a requirement to analyze the traffic going across the device, alert on any malicious traffic, and appear as a bump in the wire. How should this be implemented?
A. Specify the BVI IP address as the default gateway for connected devices
B. Enable routing on the Cisco Firepower
C. Add an IP address to the physical Cisco Firepower interfaces
D. Configure a bridge group in transparent mode
Correct Answer: D
Q11:
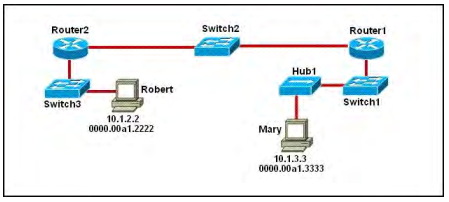
Refer to the exhibit.
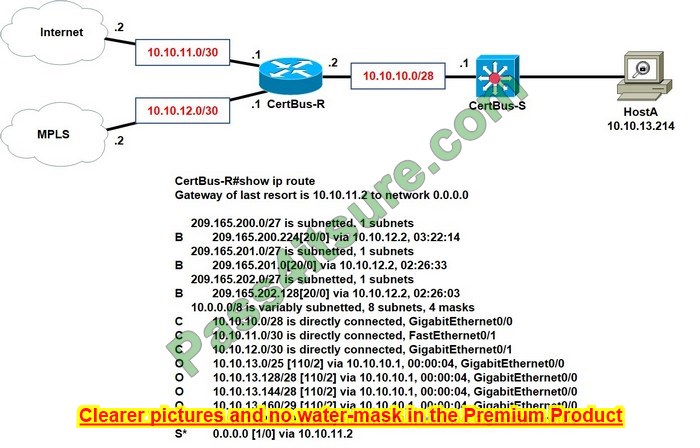
Which prefix does CertBus-R use to Host A?
A. 10.10.10.0/28
B. 10.10.13.0/25
C. 10.10.13.144/28
D. 10.10.13.208/29
Correct Answer: D
Host A address fall within the address range. However, if more than one route to the same subnet exists (the router will use the longest stick match, which matches a more specific route to the subnet). If there are routes 10.10.13.192/26 and 10.10.13.208/29, the router will forward the packet to /29 rather than /28.
Q12:
Which WLC interface provides out-of-band management in the Cisco Unified Wireless Network Architecture?
A. AP-Manager
B. service port
C. dynamic
D. virtual
Correct Answer: B
Q13:
Which statement about LLDP is true?
A. It is a Cisco proprietary protocol.
B. It is configured in global configuration mode.
C. The LLDP update frequency is a fixed value.
D. It runs over the transport layer.
Correct Answer: B
Q14:
A port security violation has occurred on a switch port due to the maximum MAC address count being exceeded, which command must be configured to increment the security-violation count and forward an SNMP trap?
A. switch port port-security violation access
B. switch port port-security violation protect
C. switch port port-security violation restrict
D. switch port port-security violation shutdown
Correct Answer: D
Q15:
Which cipher is supported for wireless encryption only with the WPA2 standard?
A. AES256
B. AES
C. RC4
D. SHA
Correct Answer: B
For more exam questions, you’ll need to download the Pass4itSure 200-301 dumps https://www.pass4itsure.com/200-301.html