What is the max time gap allowed between Cisco ICND1 & ICND2 100-105 dumps exams? The Cisco Interconnecting Cisco Networking Devices Part 1 (ICND1 v3.0) (100-105 ICND1) exam is a 90 Minutes (45-55 questions) assessment in pass4itsure that is associated with the CCENT, CCNA Routing & Switching, CCDA, CCNA Security, CCNA Wireless certification. Discount Cisco 100-105 dumps ICND1 pdf exams video answers Cisco Interconnecting Cisco Networking Devices Part 1 for download. “Cisco Interconnecting Cisco Networking Devices Part 1 (ICND1 v3.0)” is the exam name of Pass4itsure Cisco 100-105 dumps test which designed to help candidates prepare for and pass the Cisco 100-105 exam. Passing the CCIE 100-105 exam was so easy. But, it was all possible just because of dumpsbuzz I got Cisco 100-105 new questions with accurate answers from Pass4itsure. They were amazing and I found all the CCIE https://www.pass4itsure.com/100-105.html dumps questions and answers quite accurate. Thumbs up! I will recommend Pass4itsure to everyone who is taking this CCIE 100-105 exam.
[Free Cisco 100-105 Dumps&PDF From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWeVQ5WUxjZG1Idnc
[Free Microsoft 70-346 Dumps&PDF From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWUW5ITWJYd1lUZHc

Pass4itsure Latest and Most Accurate Cisco 100-105 Dumps Exam Q&As:
Question No : 11 – (Topic 1) Refer to the exhibit.
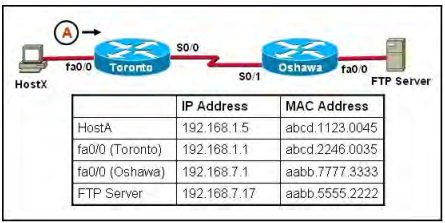
HostX is transferring a file to the FTP server. Point A represents the frame as it goes toward the Toronto router. What will the Layer 2 destination address be at this point?
A. abcd.1123.0045
B. 192.168.7.17
C. aabb.5555.2222
D. 192.168.1.1
E. abcd.2246.0035
100-105 exam Answer: E
Explanation:
For packets destined to a host on another IP network, the destination MAC address will be the LAN interface of the router. Since the FTP server lies on a different network, the host will know to send the frame to its default gateway, which is Toronto.
Question No : 12 – (Topic 1) Refer to the exhibit.
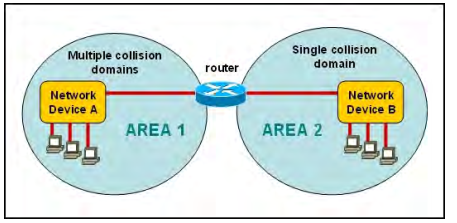
A network has been planned as shown. Which three statements accurately describe the areas and devices in the network plan? (Choose three.)
A. Network Device A is a switch.
B. Network Device B is a switch.
C. Network Device A is a hub.
D. Network Device B is a hub.
E. Area 1 contains a Layer 2 device.
F. Area 2 contains a Layer 2 device.
Answer: A,D,E
Explanation:
Switches use a separate collision domain for each port, so device A must be a switch. Hubs, however, place all ports in the same collision domain so device B is a hub. Switches reside in layer 2 while hubs are layer 1 devices.
Question No : 13 – (Topic 1) Which layer of the TCP/IP stack combines the OSI model physical and data link layers?
A. Internet layer
B. transport layer
C. application layer
D. network access layer
100-105 dumps Answer: D
Explanation:
The Internet Protocol Suite, TCP/IP, is a suite of protocols used for communication over the internet. The TCP/ IP model was created after the OSI 7 layer model for two major reasons. First, the foundation of the Internet was built using the TCP/IP suite and through the spread of the World Wide Web and Internet, TCP/IP has been preferred. Second, a project researched by the Department of Defense (DOD) consisted of creating the TCP/IP protocols. The DOD’s goal was to bring international standards which could not be met by the OSI model. Since the DOD was the largest software consumer and they preferred the TCP/IP suite, most vendors used this model rather than the OSI. Below is a side by side comparison of the TCP/IP and OSI models.
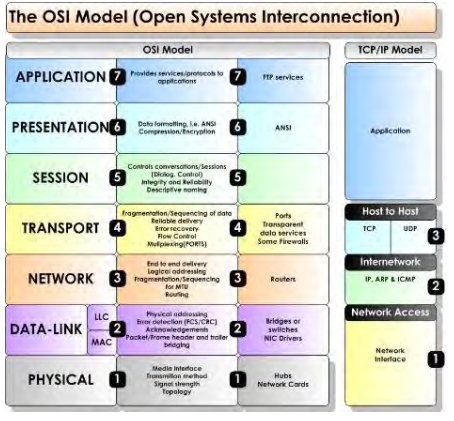
Question No : 14 – (Topic 1) Refer to the exhibit.
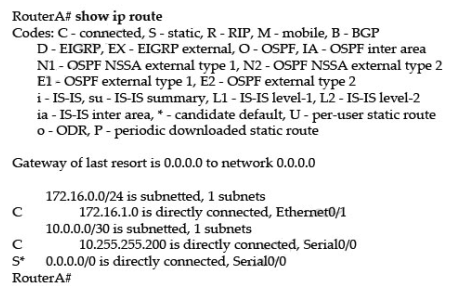
The output is from a router in a large enterprise. From the output, determine the role of the router.
A. A Core router.
B. The HQ Internet gateway router.
C. The WAN router at the central site.
D. Remote stub router at a remote site.
Answer: D
Explanation:
Since the routing table shows only a single default route using the single interface serial 0/0, we know that this is most likely a remote stub site with a single connection to the rest of the network. All the other answer options would mean that this router would have more connections, and would contain more routes.
Question No : 15 – (Topic 1) Refer to the exhibit.
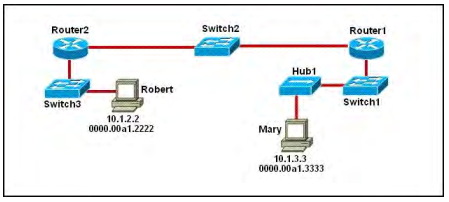
As packets travel from Mary to Robert, which three devices will use the destination MAC address of the packet to determine a forwarding path? (Choose three.)
A. Hub1
B. Switch1
C. Router1
D. Switch2
E. Router2
F. Switch3
100-105 pdf Answer: B,D,F
Explanation:
Switches use the destination MAC address information for forwarding traffic, while routers use the destination IP address information. Local Area Networks employ Layer 2 Switches and Bridges to forward and filter network traffic. Switches and Bridges operate at the Data Link Layer of the Open System Interconnect Model (OSI). Since Switches and Bridges operate at the Layer 2 they operate more intelligently than hubs, which work at Layer 1 (Physical Layer) of the OSI. Because the switches and bridges are able to listen to the traffic on the wire to examine the source and destination MAC address. Being able to listen to the traffic also allows the switches and bridges to compile a MAC address table to better filter and forward network traffic. To accomplish the above functions switches and bridges carry out the following tasks: MAC address learning by a switch or a bridge is accomplished by the same method. The switch or bridge listens to each device connected to each of its ports and scan the incoming frame for the source MAC address. This creates a MAC address to port map that is cataloged in the switches/bridge MAC database. Another name for the MAC address table is content addressable memory or CAM table. When a switch or bridge is listening to the network traffic, it receives each frame and compares it to the MAC address table. By checking the MAC table the switch/ bridge are able o determine which port the frame came in on. If the frame is on the MAC table the frame is filtered or transmitted on only that port. If the switch determines that the frame is not on the MAC table, the frame is forwarded out to all ports except the incoming port.
Question No : 16 – (Topic 1) Which two statements describe the operation of the CSMA/CD access method? (Choose two.)
A. In a CSMA/CD collision domain, multiple stations can successfully transmit data simultaneously.
B. In a CSMA/CD collision domain, stations must wait until the media is not in use before transmitting.
C. The use of hubs to enlarge the size of collision domains is one way to improve the operation of the CSMA/CD access method.
D. After a collision, the station that detected the collision has first priority to resend the lost data.
E. After a collision, all stations run a random backoff algorithm. When the backoff delay period has expired, all stations have equal priority to transmit data.
F. After a collision, all stations involved run an identical backoff algorithm and then synchronize with each other prior to transmitting data.
Answer: B,E
Explanation:
Ethernet networking uses Carrier Sense Multiple Access with Collision Detect (CSMA/CD), a protocol that helps devices share the bandwidth evenly without having two devices transmit at the same time on the network medium. CSMA/CD was created to overcome the problem of those collisions that occur when packets are transmitted simultaneously from different nodes. And trust me, good collision management is crucial, because when a node transmits in a CSMA/CD network, all the other nodes on the network receive and examine that transmission. Only bridges and routers can effectively prevent a transmission from propagating throughout the entire network! So, how does the CSMA/CD protocol work? Like this: when a host wants to transmit over the network, it first checks for the presence of a digital signal on the wire. If all is clear (no other host is transmitting), the host will then proceed with its transmission. But it doesn’t stop there. The transmitting host constantly monitors the wire to make sure no other hosts begin transmitting. If the host detects another signal on the wire, it sends out an extended jam signal that causes all nodes on the segment to stop sending data (think, busy signal). The nodes respond to that jam signal by waiting a while before attempting to transmit again. Backoff algorithms determine when the colliding stations can retransmit. If collisions keep occurring after 15 tries, the nodes attempting to transmit will then time out.
Question No : 17 – (Topic 1) Which transport layer protocol provides best-effort delivery service with no acknowledgment receipt required?
A. HTTP
B. IP
C. TCP
D. Telnet
E. UDP
100-105 vce Answer: E
Explanation:
UDP provides a connectionless datagram service that offers best-effort delivery, which means that UDP does not guarantee delivery or verify sequencing for any datagrams. A source host that needs reliable communication must use either TCP or a program that provides its own sequencing and acknowledgment services.
QUESTION NO: 18
John works as a Web Developer for ProMetaworks Inc. He creates an ASP.NET application, named MyApp1, using Visual Studio .NET. MyApp1 contains a page, named Page1. Page1 contains several TextBox controls that accept users’ input. John uses several validation controls on the page to validate input controls. He wants to display all the validation error messages on t page in a message box. However, he does not want the validation summary to be displayed inli on the Web page. What will he do to accomplish the task?
A. Add a ValidationSummary control to the page. Set its ShowMessageBox and ShowSummary properties to true.
B. Add a ValidationSummary control to the page. Set its DisplayMode property to MessageBox
C. Add a ValidationSummary control to the page. Set its ShowMessageBox property to true and ShowSummary property to false.
D. Add a CustomValidator control to the page. Write a custom client-side script function. Set the
ClientValidationFunction property of the control to the name of the function.
Answer: C
QUESTION NO: 19
David works as a Software Developer for McRobert Inc. He develops a Windows-based application, named App1, using Visual C# .NET. The application contains a Form control, name Form1. He wants to write code to initialize class-level variables, named Var1, Var2, and Var3, a soon as Form1 is instantiated. Which of the following code will he use to accomplish this?
A. private void Form1_Initialize(System.Object sender, System.EventArgs e)
{
int Var1 = 20;
int Var2 = 40;
int Var3 = 60;
}
B. private void Form1_New(System.Object sender, System.EventArgs e)
{
int Var1 = 20;
int Var2 = 40;
int Var3 = 60;
}
C. private void Form1_Load(System.Object sender, System.EventArgs e)
{
int Var1 = 20;
int Var2 = 40;
int Var3 = 60;
}
D. private void Form1_Create(System.Object sender, System.EventArgs e)
{
int Var1 = 20;
int Var2 = 40;
int Var3 = 60;
}
100-105 exam Answer: C
QUESTION NO: 20
Ryan works as a Software Developer for Mansoft Inc. He creates an ASP.NET Web application named MyWebApplication using Visual Studio .NET 2005. MyWebApplication performs validation on XML files in a directory. Whenever a new XML file appears in the directory, MyWebApplication opens the file, checks it for validation, and updates it accordingly. Ryan wants to ensure that each update performed on XML files is logged in the Web application log. He creates a String object named Var1, to store the message to be logged. Which of the following will he use to accomplish the task? Each correct answer represents a part of the solution. Choose two.
A. The EventLog.Source property
B. The EventLog.WriteEntry method
C. The Trace.WriteLine method
D. The EventLog.EventLogSource property
Answer: A,B
QUESTION NO: 21
You work as a Windows Application Developer for ABC Inc. The company uses Visual Studio.NET 2008 as its application development platform. You create a Windows Forms application using .NET Framework 3.5. You need to execute a method named ProcAmount in the background of the application. The method requires that an integer value 101 is passed to it. You are required to pass an integer value 101 to start a background thread. Which of the following code segments should you use? Each correct answer represents a part of the solution. Choose two.
A. ParameterizedThreadStart tStart;
tStart = new ParameterizedThreadStart(ProcAmount);
Thread thd = new Thread(tStart);
B. thd.Start(101);
C. ThreadStart tStart = new ThreadStart(ProcAmount);
Thread thd = new Thread(tStart, 101);
D. thd.Start();
100-105 dumps Answer: A

Owning the Pass4itsure 100-105 dumps materials is equal to have a bright future, and equal to own the key to success. “Cisco Interconnecting Cisco Networking Devices Part 1 (ICND1 v3.0)”, also known as 100-105 exam, is a Cisco certification which covers all the knowledge points of the real Cisco exam. Pass4itsure Cisco 100-105 dumps exam questions answers are updated (332 Q&As) are verified by experts. The associated certifications of 100-105 dumps is CCENT, CCNA Routing & Switching, CCDA, CCNA Security, CCNA Wireless. After you purchase Pass4itsure’s 100-105 dumps, we will provide one year free renewal service. If there’s any quality problem in https://www.pass4itsure.com/100-105.html dumps study materials or you fail 100-105 exam, we will give a full refund unconditionally.