Here, I will discuss some amazing facts about the “Pass4itsure” exam dumps preparation product, as well as Newly released Isaca CISA exam dumps, purchase discounts, use and pass the Isaca certification CISA exam at the first attempt. Pass the Isaca CISA exam (First: Exam practice test,
Second: Pass4itsure Isaca expert.) Choose: https://www.pass4itsure.com/cisa.html Study hard to pass the exam easily.
- Get success in Isaca CISA exam easily
- Pass4itsure CISA exam dumps are easy to use
- Real “Pass4itsure” Isaca CISA exam questions
- CISA exam dumps pdf and CISA exam video
- Get your money-Back in case of failure in Isaca CISA exam dumps
- Pass4itsure discount code 2020
Get Success in Isaca CISA Exam Easily
“Pass4itsure” is a well-known name. The latest Isaca CISA test questions dumps PDF practice exam. “Pass4itsure” ensures that users of their products not only gain knowledge, but also succeed in exams.

Pass4itsure CISA exam dumps are easy to use
The “Pass4itsure” product is in the form of CISA PDF dumps, CISA exam video and CISA practice exam test, which is very easy to buy and use.
Real “Pass4itsure” Isaca CISA exam questions
Practice frequently asked questions to help you pass the Isaca CISA exam at the first attempt.
QUESTION 1
The MAIN reason for requiring that all computer clocks across an organization be synchronized is to:
A. prevent omission or duplication of transactions.
B. ensure smooth data transition from client machines to servers.
C. ensure that e-mail messages have accurate time stamps.
D. support the incident investigation process.
Correct Answer: D
During an investigation of incidents, audit logs are used as evidence, and the time stamp information in them is useful. If
the clocks are not synchronized, investigations will be more difficult because a time line of events might not be easily
established. Time-stamping a transaction has nothing to do with the update itself. Therefore, the possibility of omission
or duplication of transactions does not exist. Data transfer has nothing to do with the time stamp. While the time stamp
on an e-mail may not be accurate, this is not a significant issue.
QUESTION 2
A maturity model can be used to aid the implementation of IT governance by identifying:
A. critical success factors
B. performance drivers
C. improvement opportunities
D. accountabilities
Correct Answer: C
QUESTION 3
Which of the following step of PDCA request a corrective actions on significant differences between the actual versus
the planned result?
A. Plan
B. Do
C. Check
D. Act
Correct Answer: D
Act – Request corrective actions on significant differences between actual and planned results. Analyze the differences
to determine their root causes. Determine where to apply changes that will include improvement of the process or product.
When a pass through these four steps does not result in the need to improve, the scope to which PDCA is applied may
be refined to plan and improve with more detail in the next iteration of the cycle, or attention needs to be placed in a
different stage of the process.
For your exam you should know the information below:
PDCA (plan?o?heck?ct or plan?o?heck?djust) is an iterative four-step management method used in business for the
control and continuous improvement of processes and products. It is also known as the Deming circle/cycle/wheel,
Stewart cycle, control circle/cycle, or plan?o?tudy?ct (PDSA). Another version of this PDCA cycle is OPDCA. The added
“O” stands for observation or as some versions say “Grasp the current condition.” The steps in each successive
PDCA cycle are:
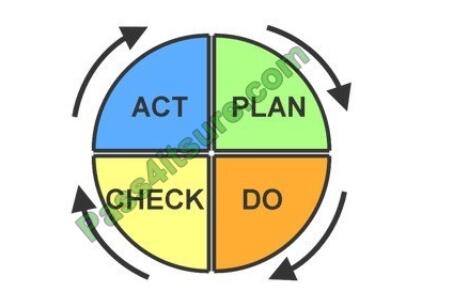
“CHECK” and “ACT” steps.
CHECK – Study the actual results (measured and collected in “DO” above) and compare against the expected results
(targets or goals from the “PLAN”) to ascertain any differences
The following reference(s) were/was used to create this question:
CISA review manual 2014 page number 107
QUESTION 4
Which of the following access control situations represents the MOST serious control weakness?
A. Computer operators have access to system level flowcharts.
B. Programmers have access to development hardware.
C. End users have access to program development tools.
D. System developers have access to production data.
Correct Answer: C
QUESTION 5
Which of the following penetration tests would MOST effectively evaluate incident handling and response capabilities of
an organization?
A. Targeted testing
B. External testing
C. internal testing
D. Double-blind testing
Correct Answer: D
In a double-blind test, the administrator and security staff are not aware of the test, which will result in an assessment of
the incident handling and response capability in an organization. In targeted, external, and internal testing, the system
administrator and security staff are aware of the tests since they are informed before the start of the tests.
QUESTION 6
An organization has implemented a disaster recovery plan. Which of the following steps should be carried out next?
A. Obtain senior management sponsorship.
B. Identify business needs.
C. Conduct a paper test.
D. Perform a system restore test.
Correct Answer: C
A best practice would be to conduct a paper test. Senior management sponsorship and business needs identification
should have been obtained prior to implementing the plan. A paper test should be conducted first, followed by system or
full testing.
QUESTION 7
An IS auditor is reviewing the physical security measures of an organization. Regarding the access card system, the IS
auditor should be MOST concerned that:
A. nonpersonalized access cards are given to the cleaning staff, who use a sign-in sheet but show no proof of identity.
B. access cards are not labeled with the organization\\’s name and address to facilitate easy return of a lost card.
C. card issuance and rights administration for the cards are done by different departments, causing unnecessary lead
time for new cards.
D. the computer system used for programming the cards can only be replaced after three weeks in the event of a
system failure.
Correct Answer: A
Physical security is meant to control who is entering a secured area, so identification of all individuals is of utmost
importance. It is not adequate to trust unknown external people by allowing them to write down their alleged name
without proof, e.g., identity card, driver\\’s license. Choice B is not a concern because if the name and address of the
organization was written on the card, a malicious finder could use the card to enter the organization\\’s premises.
Separating card issuance from technical rights management is a method to ensure a proper segregation of duties so
that no single person can produce a functioning card for a restricted area within the organization\\’s premises. Choices B
and C are good practices, not concerns. Choice D may be a concern, but not as important since a system failure of the
card programming device would normally not mean that the readers do not function anymore. It simply means that no
new cards can be issued, so this option is minor compared to the threat of improper identification.
QUESTION 8
To restore service at a large processing facility after a disaster, which of the following tasks should be performed
FIRST?
A. Launch the emergency action team.
B. Inform insurance company agents.
C. Contact equipment vendors.
D. Activate the reciprocal agreement.
Correct Answer: A
QUESTION 9
Back Orifice is an example of:
A. a virus.
B. a legitimate remote control software.
C. a backdoor that takes the form of an installed program.
D. an eavesdropper.
E. None of the choices.
Correct Answer: C
“A backdoor may take the form of an installed program (e.g., Back Orifice) or could be in the form of an existing
“”legitimate”” program, or executable file. A specific form of backdoors are rootkits, which replaces system binaries
and/or hooks into the function calls of the operating system to hide the presence of other programs, users, services and
open ports.”
QUESTION 10
Which of the following methods of encryption has been proven to be almost unbreakable when correctly used?
A. key pair
B. Oakley
C. certificate
D. 3-DES
E. one-time pad
F. None of the choices.
Correct Answer: E
Explanation: It\\’s possible to protect messages in transit by means of cryptography. One method of encryption – the onetime pad –has been proven to be unbreakable when correctly used. This method uses a matching pair of key- codes,
securely distributed, which are used once-and-only-once to encode and decode a single message. Note that this
method is difficult to use securely, and is highly inconvenient as well.
QUESTION 11
Which of the following BEST characterizes a mantrap or deadman door, which is used as a deterrent control for the
vulnerability of piggybacking?
A. A monitored double-doorway entry system
B. A monitored turnstile entry system
C. A monitored doorway entry system
D. A one-way door that does not allow exit after entry
Correct Answer: A
A monitored double-doorway entry system, also referred to as a mantrap or deadman door, is used a deterrent control
for the vulnerability of piggybacking.
QUESTION 12
Ensuring that security and control policies support business and IT objectives is a primary objective of:
A. An IT security policies audit
B. A processing audit
C. A software audit
D. A vulnerability assessment
Correct Answer: A
Ensuring that security and control policies support business and IT objectives is a primary objective of an IT security
policies audit.
QUESTION 13
Which of the following statement correctly describes the difference between symmetric key encryption and asymmetric
key encryption?
A. In symmetric key encryption the same key is used for encryption and decryption where as asymmetric key uses
private key for encryption and decryption
B. In symmetric key encryption the public key is used for encryption and the symmetric key for decryption. Where as in
asymmetric key encryption the public key is used for encryption and private key is used for decryption
C. In symmetric key encryption the same key is used for encryption and decryption where as in asymmetric key
encryption the public key is used for encryption and private key is used for decryption.
D. Both uses private key for encryption and the decryption process can be done using public key
Correct Answer: C
There are two basic techniques for encrypting information: symmetric encryption (also called secret key encryption) and
asymmetric encryption (also called public key encryption.)
Symmetric Encryption Symmetric encryption is the oldest and best-known technique. A secret key, which can be a
number, a word, or just a string of random letters, is applied to the text of a message to change the content in a
particular way. This might be as simple as shifting each letter by a number of places in the alphabet. As long as both
sender and recipient know the secret key, they can encrypt and decrypt all messages that use this key.
Few examples of symmetric key algorithms are DES, AES, Blowfish, etc
Asymmetric Encryption The problem with secret keys is exchanging them over the Internet or a large network while preventing them from falling into the wrong hands. Anyone who knows the secret key can decrypt the message. One
answer is the usage of asymmetric encryption, in which there are two related keys, usually called a key pair. The public
key is made freely available to anyone who might want to send you a message. The second key, called the private key
is kept secret, so that only you know it.
Any message (text, binary files, or documents) that are encrypted using the public key can only be decrypted by the
matching private key. Any message that is encrypted by using the private key can only be decrypted by using the
matching public key.
This means that you do not have to worry about passing public keys over the Internet (the keys are supposed to be
public).A problem with asymmetric encryption, however, is that it is slower than symmetric encryption. It requires far
more processing power to both encrypt and decrypt the content of the message.
Few examples of asymmetric key algorithms are RSA, Elliptic key Cryptography (ECC), El Gamal, Differ-Hellman, etc
The following were incorrect answers:
The other options don\\’t describe correctly the difference between symmetric key and asymmetric key encryption.
The following reference(s) were/was used to create this question:
CISA review manual 2014 Page number 348 and 349 http://support.microsoft.com/kb/246071
CISA exam dumps pdf and CISA exam video
CISA exam dumps pdf free download:
[free pdf] CISA exam dumps pdf https://drive.google.com/file/d/1_nixcCbi1_A7dJ8xkfS3tpO3JAAFmnBY/view?usp=sharing
You may be interested in other exam dumps! click here.
Get your money-Back in case of failure in Isaca CISA exam dumps
“Pass4itsure” ensures that when using CISA test questions, users can pass the test in the first attempt. However, in any case, if you fail, you can apply for your money. Now you don’t need to worry about your money loss.
Pass4itsure discount code 2020

P.S.
Know how important your time is, so that’s why you didn’t waste time. Here is for you, free of charge The latest and effective Isaca CISA exam dumps, Isaca CISA exam questions, CISA exam video.
The following is the link to get the complete CISA exam dumps https://www.pass4itsure.com/cisa.html
Full Isaca Series Certification Exam Questions Free Share: https://www.actual4tests.com/?s=Isaca
2020 Latest Pass4itsure CISA PDF and CISA VCE Dumps Free Share: https://drive.google.com/file/d/1_nixcCbi1_A7dJ8xkfS3tpO3JAAFmnBY/view?usp=sharing