This article not only shares some passing advice for the Microsoft SC-400 exam but also brings you practical solutions. To pass the SC-400 exam, you can improve your chances of passing the exam by downloading the Pass4itSure SC-400 dumps and taking a practice exam.
The latest SC-400 dumps https://www.pass4itsure.com/sc-400.html consists of 154 brand-new practice questions, presented in PDF and VCE mode, the best learning materials you deserve.
The SC-400 exam is Microsoft’s security certification exam that covers Azure security, authentication and access management, platform protection, data and application protection, and more.
Here are some suggestions for passing the SC-400 exam:
- Familiarize yourself with the exam content: Before the exam, be sure to fully understand the content and format of the SC-400 exam.
You can check the exam guide and syllabus on Microsoft’s website to help you better prepare.
- Learning-related knowledge areas: Learn about Microsoft security products and services related to the exam, such as Azure AD, Azure Sentinel, Azure Security Center, etc.
Make sure you have some understanding and proficiency in Azure infrastructure, network security, authentication, access control, data protection, application security, and more.
- Brush questions and practice tests: Doing some practice tests and practice questions before the exam can help you better understand the difficulty and test points of the test, and improve your speed and accuracy in answering questions.
- Resources can be found on Microsoft’s official training website or on other online education platforms. Also available below, the latest free exam questions from the Pass4itSure SC-400 dumps are available.
- Stay calm: It is very important to stay calm and focused during the exam.
If you encounter a question you’re not sure about, skip it and answer the others, and finally take time to think carefully. At the same time, pay attention to time management.
The rest of the time, study.
Prepare fresh SC-400 exam materials for you
SC-400 dumps free online practice questions
Question 1:
Each product group at your company must show a distinct product logo in encrypted emails instead of the standard Microsoft Office 365 logo. What should you do to create the branding templates?
A. Create a Transport rule.
B. Create an RMS template.
C. Run the Set-IRMConfiguration cmdlet.
D. Run the New-OMEConfiguration cmdlet.
Correct Answer: D
Question 2:
Your company manufactures parts that are each assigned a unique 12-character alphanumeric serial number. Emails between the company and its customers reference the serial number.
You need to ensure that only Microsoft Exchange Online emails containing the serial numbers are retained for five years.
Which three objects should you create? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. a sensitivity label
B. a retention policy
C. an auto-labeling policy
D. a trainable classifier
E. a sensitive info type
F. a retention label
G. a data loss prevention (DLP) policy
Correct Answer: CEF
C: One of the most powerful features of retention labels is the ability to apply them automatically to content that matches specified conditions.
F: You can apply retention labels to content automatically when that content contains: Specific types of sensitive information Specific keywords or searchable properties that match a query you create A match for trainable classifiers
E: Sensitive information types are pattern-based classifiers. They detect sensitive information like social security, credit card, or bank account numbers to identify sensitive items. Custom-sensitive information types use regular expressions, keywords, and keyword dictionaries.
https://docs.microsoft.com/en-us/microsoft-365/compliance/retention?view=o365-worldwide
Question 3:
HOTSPOT
You have the files shown in the following table.
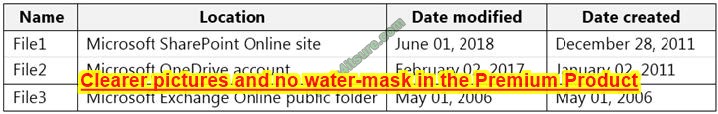
You configure a retention policy as shown in the exhibit.
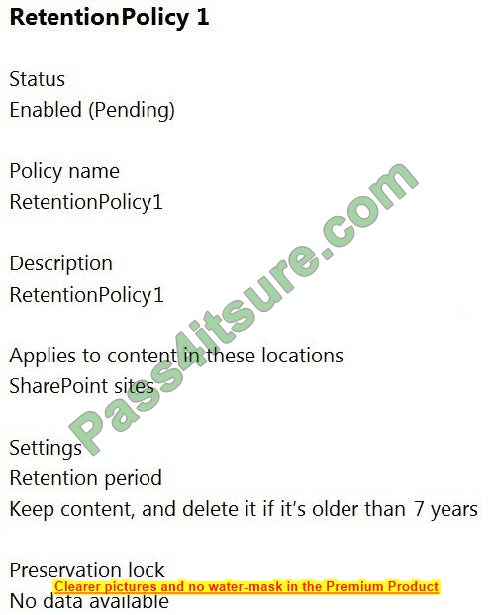
The start of the retention period is based on when items are created. The current date is January 01, 2021.
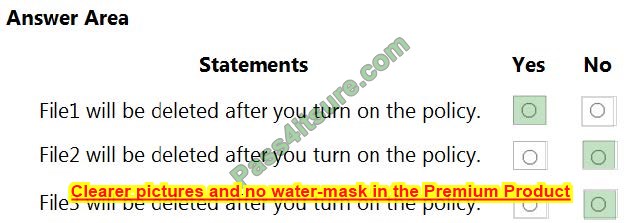
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
Question 4:
You have a Microsoft 365 tenant that uses trainable classifiers.
You are creating a custom trainable classifier.
You collect 300 sample file types from various geographical locations to use as seed content. Some of the file samples are encrypted.
You organize the files into categories as shown in the following table.
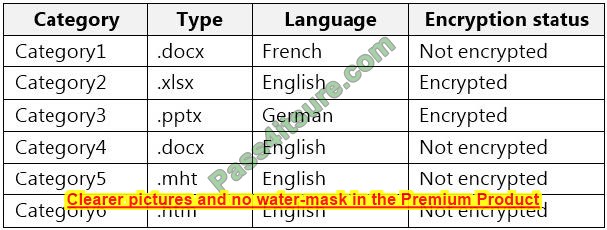
Which file categories can be used as seed content?
A. Category2, Category3, and Category5 only
B. Category1 and Category3 only
C. Category4 and Category6 only
D. Category4 and Category5 only
Correct Answer: C
Question 5:
You implement Microsoft 365 Endpoint data loss prevention (Endpoint DLP).
You have computers that run Windows 10 and have Microsoft 365 Apps installed. The computers are joined to Azure Active Directory (Azure AD).
You need to ensure that Endpoint DLP policies can protect content on the computers.
Solution: You onboard the computers to Microsoft Defender fur Endpoint.
Does this meet the goal?
A. Yes
B. No
Correct Answer: A
Question 6:
HOTSPOT
You have a Microsoft 365 tenant that uses a domain named contoso.com.
A user named User1 leaves your company. The mailbox of User1 is placed on Litigation Hold, and then the account of User1 is deleted from Azure Active Directory (Azure AD).
You need to copy the content of the User1 mailbox to a folder in the existing mailbox of another user named User2.
How should you complete the PowerShell command? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
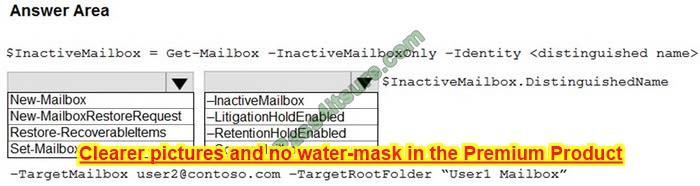
Correct Answer:
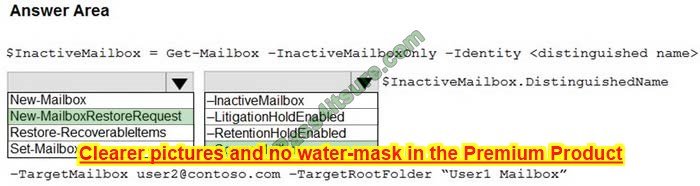
References: https://docs.microsoft.com/en-us/microsoft-365/compliance/restore-an-inactive-mailbox?view=o365-worldwide
Question 7:
HOTSPOT
You create a retention policy as shown in the following exhibit.

A user named User1 deletes a file named File1.docx from a Microsoft SharePoint Online site named Site1.
A user named User2 deletes an email and empties the Deleted Items folder in Microsoft Outlook.
Where is the content retained one year after deletion? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
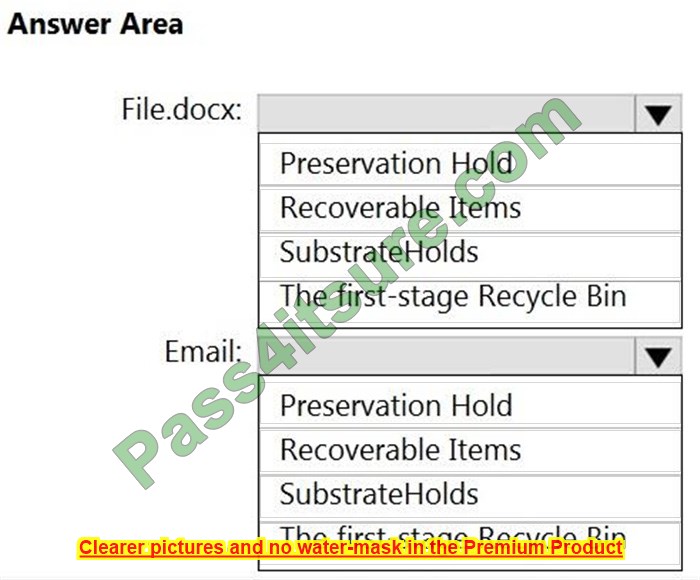
Correct Answer:
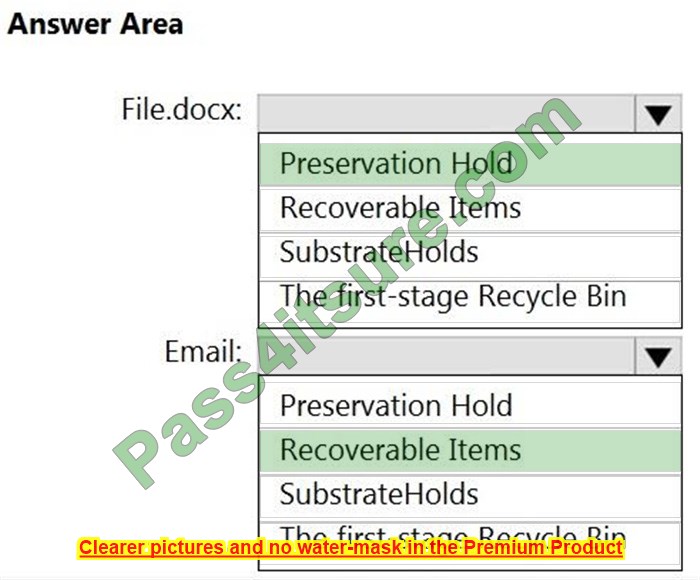
Question 8:
HOTSPOT You create a retention label policy named Contoso_Policy that contains the following labels:
1. 10 years then delete
2. 5 years then delete
3. Do not retain
Contoso_Policy is applied to content in Microsoft SharePoint Online sites.
After a couple of days, you discover the following messages on the Properties page of the label policy:
1. Status: Off (Error)
2. It\’s taking longer than expected to deploy the policy
You need to reinitiate the policy.
How should you complete the command? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
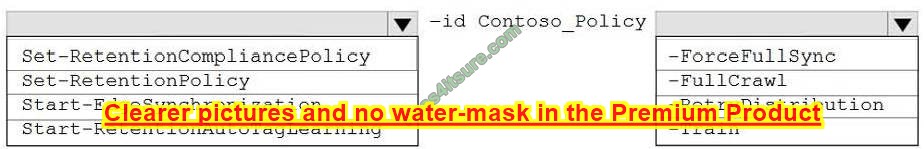
Correct Answer:
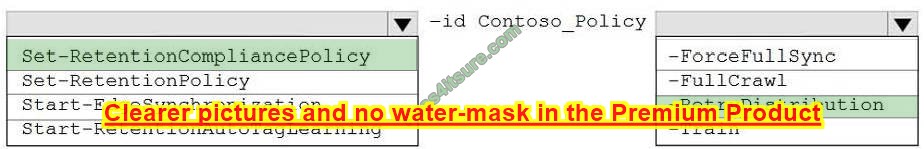
Question 9:
HOTSPOT
You have a Microsoft 365 E5 subscription that contains the devices shown in the following table.
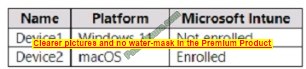
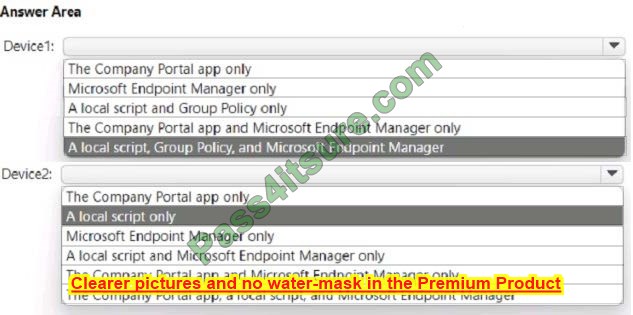
You need to onboard the devices to Microsoft Purview. The solution must ensure that you can apply Endpoint data loss prevention (Endpoint DLP) policies to the devices. What can you use to onboard each device? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
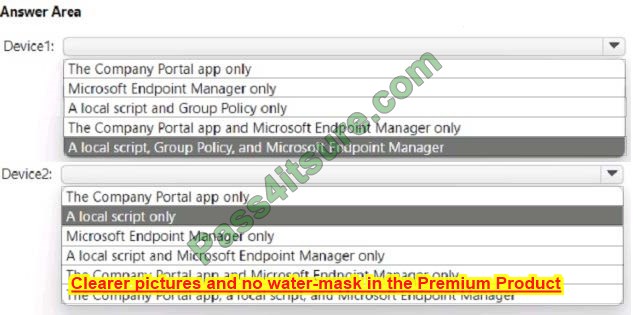
Correct Answer:
Question 10:
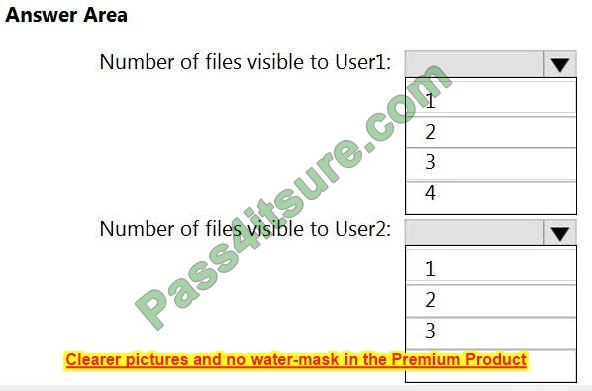
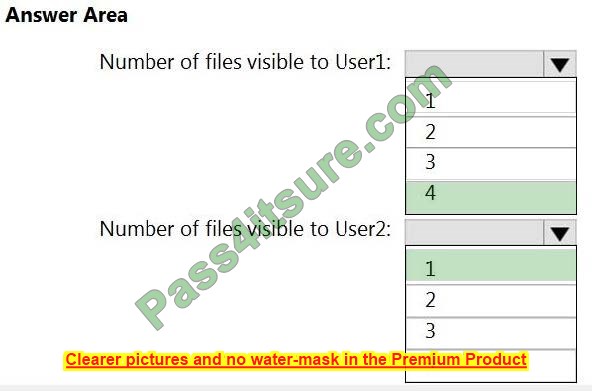
HOTSPOT
How many files in Site2 will be visible to User1 and User2 after you turn on DLPpolicy1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
Question 11:
HOTSPOT
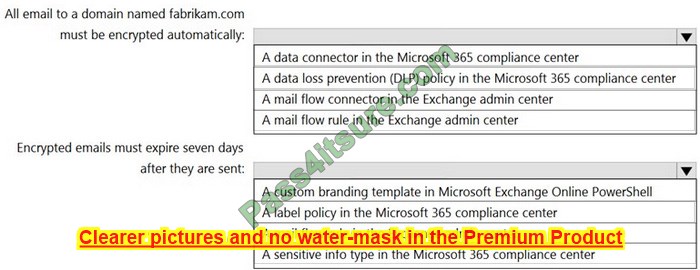
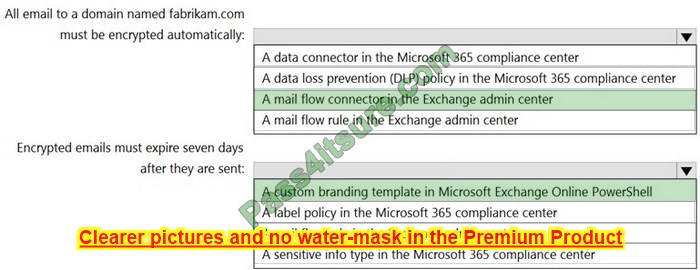
You are implementing Microsoft Office 365 Message Encryption (OME) for a Microsoft 365 tenant named contoso.com.
You need to meet the following requirements:
1. All emails to a domain named fabrikam.com must be encrypted automatically.
2. Encrypted emails must expire seven days after they are sent.
What should you configure for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/email-encryption?view=o365-worldwide
Question 12:
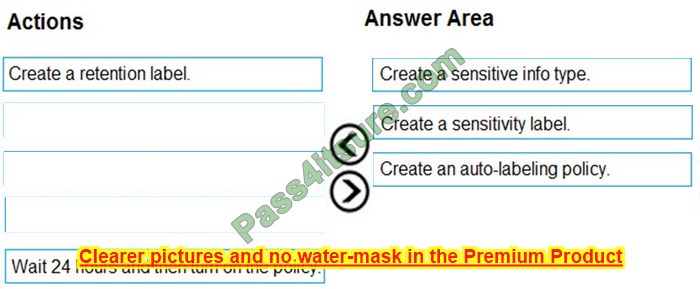
DRAG DROP
You need to meet the technical requirements for the Site1 documents.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:
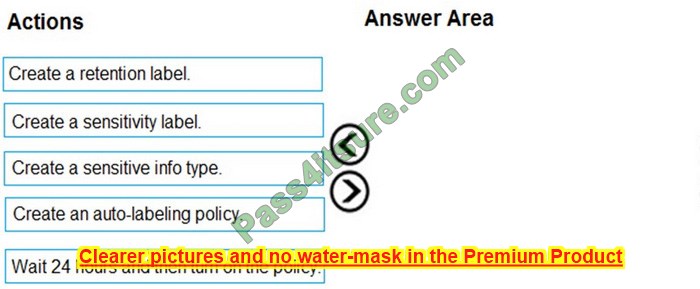
Correct Answer:
Question 13:
You are configuring a retention label named Label1 as shown in the following exhibit.
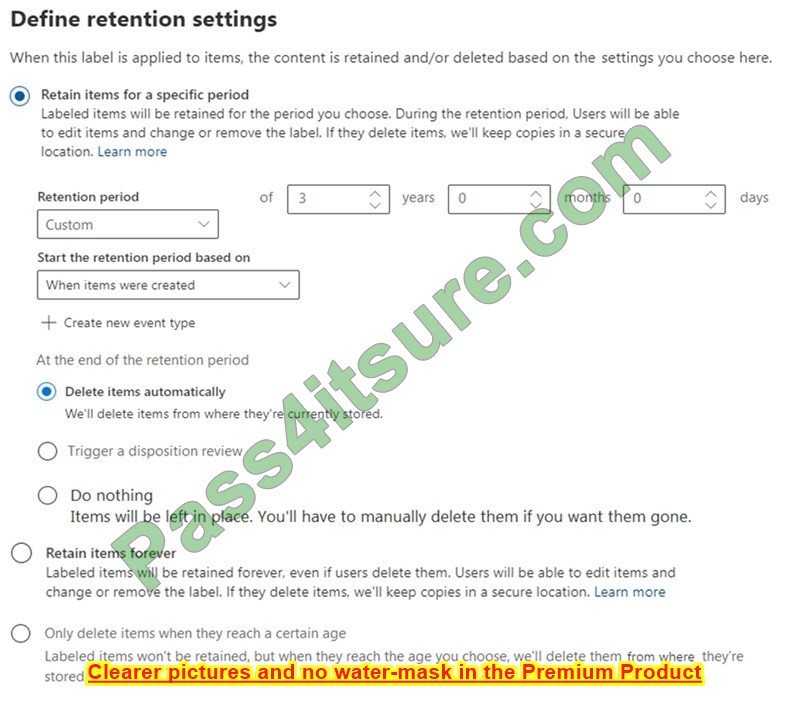
You need to ensure that documents that have Label1 applied are deleted three years after the end of your company\’s fiscal year. What should you do?
A. Create a new event type.
B. Select Only delete items when they reach a certain age.
C. Modify the Retention period setting.
D. Set At the end of the retention period to Trigger a disposition review.
Correct Answer: A
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/event-driven-retention?view=o365-worldwide
Question 14:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear on the review screen.
You are configuring a file policy in Microsoft Cloud App Security.
You need to configure the policy to apply to all files. Alerts must be sent to every file owner who is affected by the policy. The policy must scan for credit card numbers, and alerts must be sent to the Microsoft Teams site of the affected department.
Solution: You use the Built-in DLP inspection method and send alerts to Microsoft Power Automate.
Does this meet the goal?
A. Yes
B. No
Correct Answer: A
Reference: https://docs.microsoft.com/en-us/cloud-app-security/content-inspection-built-in https://docs.microsoft.com/en-us/cloud-app-security/flow-integration
Question 15:
You need to be alerted when users share sensitive documents from Microsoft One Drive with any users outside your company. What should you do?
A. From the Exchange admin center, create a data loss prevention (DLP) policy.
B. From the Azure portal, create an Azure Active Directory (Azure AD) Identity Protection policy.
C. From the Microsoft 365 compliance center, create an insider risk policy.
D. From the Cloud App Security portal, create a file policy.
Correct Answer: A
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/dlp-learn-about-dlp?view=o365-worldwide
SC-400 questions pdf free download:
https://drive.google.com/file/d/1k7T6S818xcR8k_UAlN85UpSKervW6QLB/view?usp=share_link
These are just some of the questions, and you need to go to Pass4itSure for the whole thing.
Conclusion:
To do the above exam recommendations, in conjunction with the latest SC-400 dumps, the full SC-400 question https://www.pass4itsure.com/sc-400.html is available for online download
With these, successfully passing the Microsoft Information Protection Administrator exam is easy.