How can I get latest CompTIA SY0-501 exam Material? https://www.pass4itsure.com/sy0-501.html is a great site where you can find all types of materials related to actual problems.SY0-501 exam dumps Updated: Mar 20, 2020.
We Can Share All The New Material: Verified And Latest CompTIA SY0 -501 exam dumps!
Download REAL SY0-501 PDF Dumps Training Material Now – Ensure Your Success in CompTIA Exam
SY0-501 PDF Dumps [2020] https://drive.google.com/open?id=1ha5qYtI5h6Ft9bhr3cRN-pn8gxjbRR2W
SY0-501 PDF Dumps https://drive.google.com/open?id=1zeg1_QgEd8U3Q3Woc1Ewk8ysWDIXULKT

Yes, it is true that Pass4itsure has new and up-to-date exam dumps, as it is your most reliable resource for certification exams. Now also offers an exclusive discount of 12%, don’t you act?
Get valid CompTIA Server+ SK0-004 dumps For Free 2020
CompTIA Security+ Exam Codes SY0-501
CompTIA Security+ is the first security certification IT professionals should earn. It establishes the core knowledge required of any cybersecurity role and provides a springboard to intermediate-level cybersecurity jobs.
https://www.comptia.org/certifications/security
Updated CompTIA SY0-501 Questions & Answers (2020)
To get the best score on the SY0-501 exam, you need to experience the type of SY0-501 exam that will be answered and prepare the SY0-501 exam for a SY0-501 PDF dumps of each topic.
QUESTION 1
A mobile device user is concerned about geographic positioning information being included in messages sent between
users on a popular social network platform. The user turns off the functionality in the application, but wants to ensure the
application cannot re-enable the setting without the knowledge of the user.
Which of the following mobile device capabilities should the user disable to achieve the stated goal?
A. Device access control
B. Location based services
C. Application control
D. GEO-Tagging
Correct Answer: D
QUESTION 2
A security auditor is putting together a report for the Chief Executive Officer (CEO) on personnel security and its impact
on the security posture of the whole organization. Which of the following would be the MOST important factor to
consider when it comes to personnel security?
A. Insider threats
B. Privilege escalation
C. Hacktivist
D. Phishing through social media
E. Corporate espionage
Correct Answer: A
QUESTION 3
Two users need to send each other emails over unsecured channels. The system should support the principle of nonrepudiation. Which of the following should be used to sign the user\\’s certificates?
A.RA
B. CA
C. CRL
D. CSR
Correct Answer: B
QUESTION 4
A company\\’s user lockout policy is enabled after five unsuccessful login attempts. The help desk notices a user is
repeatedly locked out over the course of a workweek. Upon contacting the user, the help desk discovers the user is on
vacation and does not have network access. Which of the following types of attacks are MOST likely occurring? (Select
two.)
A. Replay
B. Rainbow tables
C. Brute force
D. Pass the hash
E. Dictionary
Correct Answer: CE
QUESTION 5
A bank is experiencing a DoS attack against an application designed to handle 500 IP-based sessions.
in addition, the perimeter router can only handle 1Gbps of traffic.
Which of the following should be implemented to prevent a DoS attacks in the future?
A. Deploy multiple web servers and implement a load balancer
B. Increase the capacity of the perimeter router to 10 Gbps
C. Install a firewall at the network to prevent all attacks
D. Use redundancy across all network devices and services
Correct Answer: D
QUESTION 6
A security analyst receives a notification from the IDS after working hours, indicating a spike in network traffic. Which of
the following BEST describes this type of IDS?
A. Anomaly-based
B. Stateful
C. Host-based
D. Signature-based
Correct Answer: A
QUESTION 7
A website administrator has received an alert from an application designed to check the integrity of the company\\’s
website. The alert indicated that the hash value for a particular MPEG file has changed. Upon further investigation, the
media appears to be the same as it was before the alert.
Which of the following methods has MOST likely been used?
A. Cryptography
B. Time of check/time of use
C. Man in the middle
D. Covert timing
E. Steganography
Correct Answer: E
QUESTION 8
Two users need to securely share encrypted files via email. Company policy prohibits users from sharing credentials or
exchanging encryption keys.
Which of the following can be implemented to enable users to share encrypted data while abiding by company policies?
A. Key escrow
B. Digital signatures
C. PKI
D. Hashing
Correct Answer: C
QUESTION 9
A company wants to ensure that the validity of publicly trusted certificates used by its web server can be determined
even during an extended internet outage. Which of the following should be implemented?
A. Recovery agent
B. Ocsp
C. Crl
D. Key escrow
Correct Answer: B
QUESTION 10
A security analyst is reviewing the following output from an IPS:
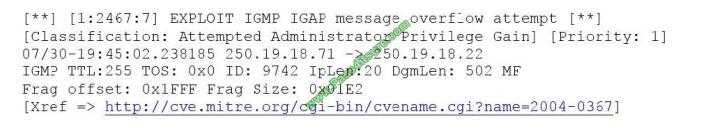
Given this output, which of the following can be concluded? (Select two.)
A. The source IP of the attack is coming from 250.19.18.22.
B. The source IP of the attack is coming from 250.19.18.71.
C. The attacker sent a malformed IGAP packet, triggering the alert.
D. The attacker sent a malformed TCP packet, triggering the alert.
E. The TTL value is outside of the expected range, triggering the alert.
Correct Answer: BC
QUESTION 11
Which of the following is the proper order for logging a user into a system from the first step to the last step?
A. Identification, authentication, authorization
B. Identification, authorization, authentication
C. Authentication, identification, authorization
D. Authentication, identification, authorization
E. Authorization, identification, authentication
Correct Answer: A
QUESTION 12
A new mobile application is being developed in-house. Security reviews did not pick up any major flaws, however
vulnerability scanning results show fundamental issues at the very end of the project cycle.
Which of the following security activities should also have been performed to discover vulnerabilities earlier in the
lifecycle?
A. Architecture review
B. Risk assessment
C. Protocol analysis
D. Code review
Correct Answer: D
QUESTION 13
An application was recently compromised after some malformed data came in via web form. Which of the following
would MOST likely have prevented this?
A. Input validation
B. Proxy server
C. Stress testing
D. Encoding
Correct Answer: A
Features of Pass4itsure

Download the new, valid, factual, verified and authentic CompTIA SY0-501 exams dumps:
SY0-501 PDF Dumps [2020] https://drive.google.com/open?id=1ha5qYtI5h6Ft9bhr3cRN-pn8gxjbRR2W
SY0-501 PDF Dumps https://drive.google.com/open?id=1zeg1_QgEd8U3Q3Woc1Ewk8ysWDIXULKT
Above shared the SY0-501 exam PDF & SY0-501 exam video & practice questions 2020 for free.Click the following URL and get the most updated questions: https://www.pass4itsure.com/sy0-501.html easy preparation of your CompTIA Project+ SY0-501 exam certification.