CASP+ is the only hands-on, performance-based certification for practitioners – not managers – at the advanced skill level of cybersecurity.
While cybersecurity managers help identify what cybersecurity policies and frameworks could be implemented, CASP+ certified professionals figure out how to implement solutions within those policies and frameworks.
We share the latest effective CompTIA CASP CAS-003 exam dumps online Practice test to improve your skills! You can also choose CAS-003 PDF ! Get the full CAS-003 dumps: https://www.pass4itsure.com/cas-003.html (Q&As: 544 ) to pass the exam easily!
[PDF] Free CompTIA CASP CAS-003 pdf dumps download from Google Drive: https://drive.google.com/open?id=1PlK-rTaAM7cKWhy4TxIAARXAbVIUQZ4m
[PDF] Free Full CompTIA pdf dumps download from Google Drive: https://drive.google.com/open?id=1SnVb1WLCtG5umIgtJ4zeNNSpuAFWZ3yg
(CASP+) Advanced Security Practitioner Certification | CompTIA IT Certifications : https://certification.comptia.org/certifications/comptia-advanced-security-practitioner
Latest effective CompTIA CASP CAS-003 Exam Practice Tests
QUESTION 1
After multiple service interruptions caused by an older datacenter design, a company decided to migrate away from its
datacenter. The company has successfully completed the migration of all datacenter servers and services to a cloud
provider. The migration project includes the following phases: Selection of a cloud provider Architectural design
Microservice segmentation Virtual private cloud Geographic service redundancy Service migration The Chief
Information Security Officer (CISO) is still concerned with the availability requirements of critical company applications.
Which of the following should the company implement NEXT?
A. Multicloud solution
B. Single-tenancy private cloud
C. Hybrid cloud solution
D. Cloud access security broker
Correct Answer: D
QUESTION 2
An ISP is peering with a new provider and wishes to disclose which autonomous system numbers should be allowed
through BGP for network transport. Which of the following should contain this information?
A. Memorandum of Understanding
B. Interconnection Security Agreement
C. Operating Level Agreement
D. Service Level Agreement
Correct Answer: B
QUESTION 3
The network administrator has been tracking the cause of network performance problems and decides to take a look at
the internal and external router stats.

Which of the following should the network administrator do to resolve the performance issue after analyzing the above
information?
A. The IP TOS field of business related network traffic should be modified accordingly.
B. The TCP flags of business related traffic should be modified accordingly.
C. An ACL should be placed on the external router to drop incoming ICMP packets.
D. An ACL should be placed on the internal router to drop layer 4 packets to and from port 0.
Correct Answer: A
QUESTION 4
Joe is a security architect who is tasked with choosing a new NIPS platform that has the ability to perform SSL
inspection, analyze up to 10Gbps of traffic, can be centrally managed and only reveals inspected application payload
data to specified internal security employees. Which of the following steps should Joe take to reach the desired
outcome?
A. Research new technology vendors to look for potential products. Contribute to an RFP and then evaluate RFP
responses to ensure that the vendor product meets all mandatory requirements. Test the product and make a product
recommendation.
B. Evaluate relevant RFC and ISO standards to choose an appropriate vendor product. Research industry surveys,
interview existing customers of the product and then recommend that the product be purchased.
C. Consider outsourcing the product evaluation and ongoing management to an outsourced provider on the basis that
each of the requirements are met and a lower total cost of ownership (TCO) is achieved.
D. Choose a popular NIPS product and then consider outsourcing the ongoing device management to a cloud provider.
Give access to internal security employees so that they can inspect the application payload data.
E. Ensure that the NIPS platform can also deal with recent technological advancements, such as threats emerging from
social media, BYOD and cloud storage prior to purchasing the product.
Correct Answer: A
A request for a Proposal (RFP) is in essence an invitation that you present to vendors asking them to submit proposals
on a specific commodity or service. This should be evaluated, then the product should be tested and then a product
recommendation can be made to achieve the desired outcome.
QUESTION 5
Company ABC is hiring customer service representatives from Company XYZ. The representatives reside at Company
XYZ\\’s headquarters. Which of the following BEST prevents Company XYZ representatives from gaining access to
unauthorized Company ABC systems?
A. Require each Company XYZ employee to use an IPSec connection to the required systems
B. Require Company XYZ employees to establish an encrypted VDI session to the required systems
C. Require Company ABC employees to use two-factor authentication on the required systems
D. Require a site-to-site VPN for intercompany communications
Correct Answer: B
VDI stands for Virtual Desktop Infrastructure. Virtual desktop infrastructure is the practice of hosting a desktop operating
system within a virtual machine (VM) running on a centralized server.
Company ABC can configure virtual desktops with the required restrictions and required access to systems that the
users in company XYZ require. The users in company XYZ can then log in to the virtual desktops over a secure
encrypted connection and then access authorized systems only.
QUESTION 6
A developer is determining the best way to improve security within the code being developed. The developer is focusing
on input fields where customers enter their credit card details. Which of the following techniques, if implemented in the
code, would be the MOST effective in protecting the fields from malformed input?
A. Client side input validation
B. Stored procedure
C. Encrypting credit card details
D. Regular expression matching
Correct Answer: D
Regular expression matching is a technique for reading and validating input, particularly in web software. This question
is asking about securing input fields where customers enter their credit card details. In this case, the expected input into
the credit card number field would be a sequence of numbers of a certain length. We can use regular expression
matching to verify that the input is indeed a sequence of numbers. Anything that is not a sequence of numbers could be
malicious code.
QUESTION 7
After being notified of an issue with the online shopping cart, where customers are able to arbitrarily change the price of
listed items, a programmer analyzes the following piece of code used by a web based shopping cart.
SELECT ITEM FROM CART WHERE ITEM=ADDSLASHES($USERINPUT);
The programmer found that every time a user adds an item to the cart, a temporary file is created on the web server
/tmp directory. The temporary file has a name which is generated by concatenating the content of the $USERINPUT
variable
and a timestamp in the form of MM-DD-YYYY, (e.g. smartphone-12-25-2013.tmp) containing the price of the item being
purchased. Which of the following is MOST likely being exploited to manipulate the price of a shopping cart\\’s items?
A. Input validation
B. SQL injection
C. TOCTOU
D. Session hijacking
Correct Answer: C
In this question, TOCTOU is being exploited to allow the user to modify the temp file that contains the price of the item.
In software development, time of check to time of use (TOCTOU) is a class of software bug caused by changes in a
system between the checking of a condition (such as a security credential) and the use of the results of that check. This
is one example of a race condition.
A simple example is as follows: Consider a Web application that allows a user to edit pages, and also allows
administrators to lock pages to prevent editing. A user requests to edit a page, getting a form which can be used to alter
its content. Before the user submits the form, an administrator locks the page, which should prevent editing. However,
since editing has already begun, when the user submits the form, those edits (which have already been made) are
accepted. When the user began editing, the appropriate authorization was checked, and the user was indeed allowed to
edit. However, the authorization was used later, at a time when edits should no longer have been allowed.
TOCTOU race conditions are most common in Unix between operations on the file system, but can occur in other
contexts, including local sockets and improper use of database transactions.
QUESTION 8
A user is suspected of engaging in potentially illegal activities. Law enforcement has requested that the user continue to
operate on the network as normal. However, they would like to have a copy of any communications from the user
involving certain key terms. Additionally, the law enforcement agency has requested that the user\\’s ongoing
communication be retained in the user\\’s account for future investigations. Which of the following will BEST meet the
goals of law enforcement?
A. Begin a chain-of-custody on for the user\\’s communication. Next, place a legal hold on the user\\’s email account.
B. Perform an e-discover using the applicable search terms. Next, back up the user\\’s email for a future investigation.
C. Place a legal hold on the user\\’s email account. Next, perform e-discovery searches to collect applicable emails.
D. Perform a back up of the user\\’s email account. Next, export the applicable emails that match the search terms.
Correct Answer: C
A legal hold is a process that an organization uses to maintain all forms of pertinent information when legal action is
reasonably expected. E-discovery refers to discovery in litigation or government investigations that manages the
exchange of electronically stored information (ESI). ESI includes email and office documents, photos, video, databases,
and other filetypes.
QUESTION 9
A software development team is conducting functional and user acceptance testing of internally developed web
applications using a COTS solution. For automated testing, the solution uses valid user credentials from the enterprise
directory to authenticate to each application. The solution stores the username in plain text and the corresponding
password as an encoded string in a script within a file, located on a globally accessible network share. The account
credentials used belong to the development team lead. To reduce the risks associated with this scenario while
minimizing disruption to ongoing testing, which of the following are the BEST actions to take? (Choose two.)
A. Restrict access to the network share by adding a group only for developers to the share\\’s ACL
B. Implement a new COTS solution that does not use hard-coded credentials and integrates with directory services
C. Obfuscate the username within the script file with encoding to prevent easy identification and the account used
D. Provision a new user account within the enterprise directory and enable its use for authentication to the target
applications. Share the username and password with all developers for use in their individual scripts
E. Redesign the web applications to accept single-use, local account credentials for authentication
Correct Answer: AB
QUESTION 10
An organization recently upgraded its wireless infrastructure to support WPA2 and requires all clients to use this
method. After the upgrade, several critical wireless clients fail to connect because they are only WEP compliant. For the
foreseeable future, none of the affected clients have an upgrade path to put them into compliance with the WPA2
requirement. Which of the following provides the MOST secure method of integrating the non-compliant clients into the
network?
A. Create a separate SSID and WEP key to support the legacy clients and enable detection of rogue APs.
B. Create a separate SSID and WEP key on a new network segment and only allow required communication paths.
C. Create a separate SSID and require the legacy clients to connect to the wireless network using certificate-based
802.1x.
D. Create a separate SSID and require the use of dynamic WEP keys.
Correct Answer: B
QUESTION 11
An engineer maintains a corporate-owned mobility infrastructure, and the organization requires that all web browsing
using corporate-owned resources be monitored. Which of the following would allow the organization to meet its
requirement? (Choose two.)
A. Exempt mobile devices from the requirement, as this will lead to privacy violations
B. Configure the devices to use an always-on IPSec VPN
C. Configure all management traffic to be tunneled into the enterprise via TLS
D. Implement a VDI solution and deploy supporting client apps to devices
E. Restrict application permissions to establish only HTTPS connections outside of the enterprise boundary
Correct Answer: BE
QUESTION 12
A security controls assessor intends to perform a holistic configuration compliance test of networked assets. The
assessor has been handed a package of definitions provided in XML format, and many of the files have two common
tags within them: “” and “”. Which of the following tools BEST supports the use of these definitions?
A. HTTP interceptor
B. Static code analyzer
C. SCAP scanner
D. XML fuzzer
Correct Answer: D
QUESTION 13
There have been several exploits to critical devices within the network. However, there is currently no process to
perform vulnerability analysis. Which the following should the security analyst implement during production hours to
identify critical threats and vulnerabilities?
A. asset inventory of all critical devices
B. Vulnerability scanning frequency that does not interrupt workflow
C. Daily automated reports of exploited devices
D. Scanning of all types of data regardless of sensitivity levels
Correct Answer: B
CASP+ covers the technical knowledge and skills required to conceptualize, engineer, integrate and implement secure solutions across complex environments to support a resilient enterprise.
Share 13 of the latest CompTIA CASP CAS-003 dumps Practice tests for free to help you improve your skills. CAS-003 PDF Download Online! Get the full CAS-003 dumps: https://www.pass4itsure.com/cas-003.html (Q&As: 544 ). Easily pass the exam!
[PDF] Free CompTIA CASP CAS-003 pdf dumps download from Google Drive: https://drive.google.com/open?id=1PlK-rTaAM7cKWhy4TxIAARXAbVIUQZ4m
[PDF] Free Full CompTIA pdf dumps download from Google Drive: https://drive.google.com/open?id=1SnVb1WLCtG5umIgtJ4zeNNSpuAFWZ3yg
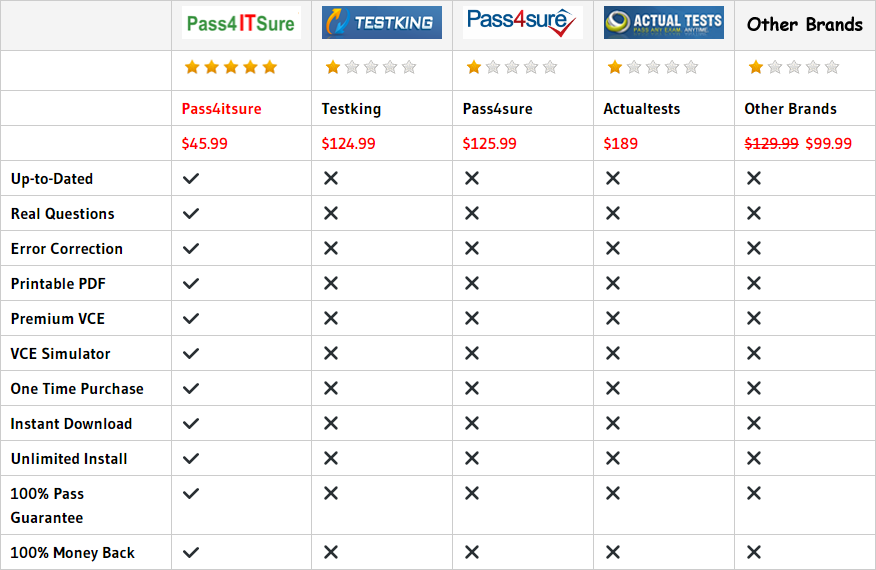
Why Pass4itsure?
related: https://www.takecertify.com/high-quality-microsoft-70-412-dumps/